
The reality that FOSDEM is expanding bears witness to how a lot more people and other, often larger, organizations are putting significant collective effort into the principle of open-source development.
Read Details
Even if zero-click spyware is a real and rising worry, the chances of falling prey to such high-tech assaults can be greatly lessened by knowing how it works and setting up strong security measures.
Read Details
While Netflix is taking all actions it can to contain the breach and ensure that it does not happen in the future, this incident has also served to raise a conversation about content security in the digital age.
Read Details
Cyberattacks like these are becoming more sophisticated and widespread. By using deceptive techniques and exploiting human trust, attackers are finding new ways to slip past defences.
Read Details
Cybersecurity is a must in today's world, not an option. The foundation on which democratic processes stand may be severely undermined without swift action and continuous investment in the protection of digital assets.
Read Details
Storm-0501's attacks show no signs of slowing down. With hybrid cloud environments becoming the norm, the threat is only growing.
Read Details
With investigations still ongoing on the breach, Star Health has a lot of rebuilding to do in gaining back the reputation and trust of customers.
Read Details
ISOAH Data Securities proudly announces its partnership with Seceon ( Comprehensive threat detection and response), a leading authority in SOC service. ISOAH becomes the Seceon 2024 Premier partner in India.
Read Details
Common source code elements between KLogEXE and FPSpy strongly indicate that the strains originate from the same malware author.
Read Details
As the demand for cybersecurity professionals' soars, this program equips students with advanced skills and real-world experience through 100% practical training, live projects, and internships.
Read Details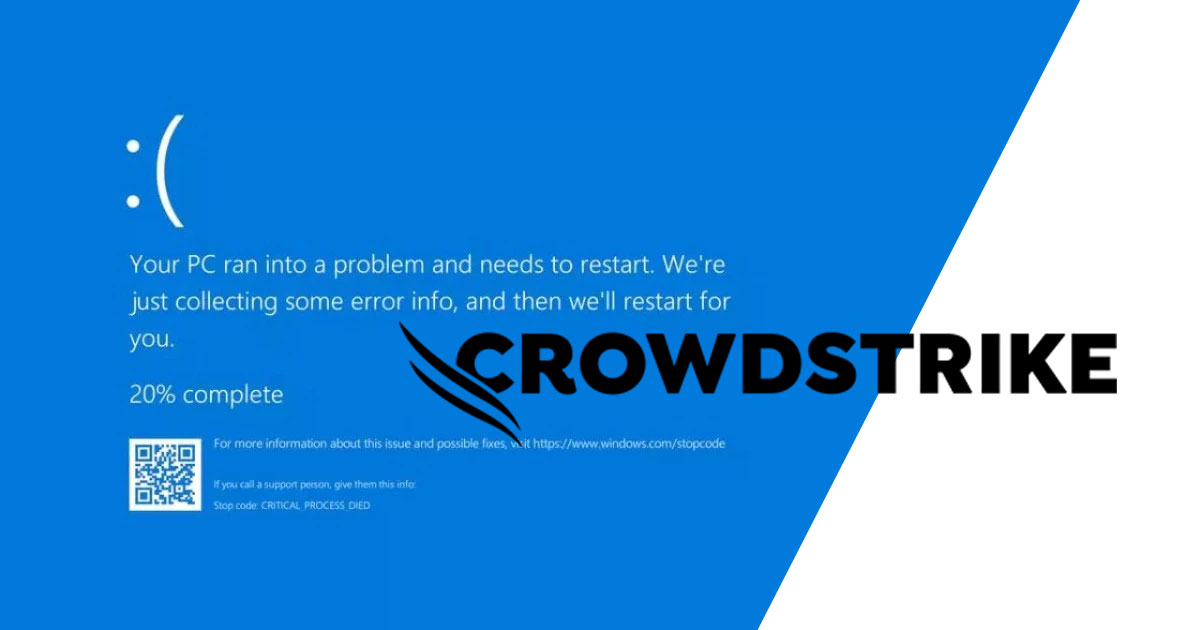
CrowdStrike was able to retain its reputation as a cybersecurity leader through a quick response to the global IT outage and by making the RCA report public.
Read Details
The 0.0.0.0 Day vulnerability is a case in point that all software, even the most trusted, may harbour security bugs.
Read Details
In a significant expansion outside India, the Indian School of Ethical Hacking (ISOEH) has partnered with DanpheLink Nepal to open the first International Centre of Excellence in Cyber Security in Kathmandu, Nepal on 8th June 2024.
Read Details
Personal information of more than over 7.5 million customers’ data is leaked and available on the dark web. As per reports, the leaked data is now available in dark web forums and is being sold for as low as $217.
Read Details
Social Media platforms like Facebook are a prime target for unethical hackers. Social media user numbers are expected to increase by 16% and reach 500 million in 2025. So definitely use Facebook but keep your eye on hackers.
Read Details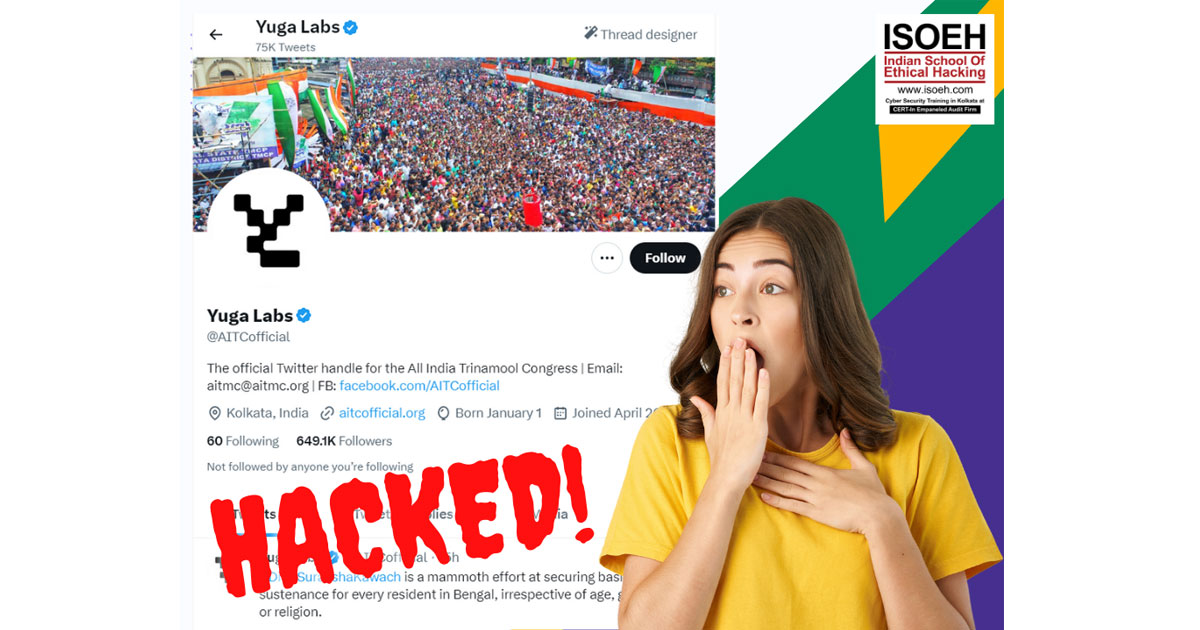
A goose bumping news. TMC's Twitter account got hacked! Do you know your account can be hacked at any time?
Read Details
A shocking update! Hackers have not only impeded AIIMS Delhi and power grids, but they have also intervened majorly in the Twitter account of India’s Jal Shakti on 28th December 2022. With this, they attacked for the second time and utilized it by promoting scams, retweeting, and liking from several bot accounts.
Read Details
The online gaming market in India is booming at an exponential rate. Covid times has added to it because the work-from-home scenario and people sitting at home have even promoted and persuaded people to tend toward the gaming industry.
Read Details
Europol offers over a hundred free decoding tools to help release detainee files from cyber criminals in order to protect organizations and individuals from the ever-increasing peril of Ransomware. To date, this scheme has helped over 1.5 million users successfully decrypt their devices without any payment to any agencies.
Read Details
A Crypto mining group named 'The 8220' has enlarged in size to surround as many as 30,000 contaminated hosts. Victims are identified by their internet accessibility but not targeted geographically. The 8220 Troop is one of such low-skill cybercriminal gangs that have been noticed to infect cloud hosts and drive a botnet and cryptocurrency miners.
Read Details
Cleartrip is the airline and hotel booking website owned by Flipkart, which recently suffered a severe data breach in its internal system. They have asked the customers to reset their passwords as a precautionary measure.
Read Details
Apple announced it plans to launch an enhanced security setting called Lockdown Mode in iOS 16, iPad OS 16, and macOS Ventura to protect high-risk users against mostly targeted cybercrimes. Activating the Lockdown Mode, "strengthens device protections and strictly prohibits some functionalities, steeply minimizing the attack surface that potentially could be exploited by highly targeted rapacious spyware," as per the statement given by Apple.
Read Details
A former Amazon employee, Ms. Paige Thompson, 36-year-old, from U.S was accused of wire fraud and computer intrusions for her action in the theft of personal data of more than 100 million people in the 2019 Capital One breach. She is line up for sentencing on September 15, 2022. Mounting to punishable by up to 25 years in prison for the offenses.
Read Details
A cyber-attack instigates against India by a Malaysia-based group of hackers reinforce Tuesday with around 200 Indian government and private domains, including companies linked to the banking sector, impending under attack. According to the researchers, the tool used by the hackers allows them to vandalize any target website at their will. The tool is named Script Deface (SC Deface) and permits a user to download it and make changes to the HTML code.
Read Details
This time of the year tourists rush has been witnessed for Char Dham Yatra or Mata Vaishno Devi darshan, and cyber criminals now dupe money from tourists on the pretext of booking them chopper rides for the pilgrimage. There are websites that look alike like some known popular travel and tour agencies and offer cheap pilgrimage packages or helicopter rides during the visit at very low rates.
Read Details
An advanced persistent threat (APT) actor line up with Chinese state interests has been observed armed with the new zero-day flaw in Microsoft Office to gain code execution on affected systems. TA413 CN APT mottled [in-the-wild] exploiting the Follina zero-day using URLs to deliver ZIP archives that contain Word Documents that use the technique of enterprise security firm Proofpoint.
Read Details
Different versions of a WordPress plugin in the name of "School Management Pro" sheltered a secret door that could take full rival control over vulnerable websites. As soon as the secret door has since been abolished, the exact origins of the compromise remain fuzzy, with the vendor as they said that they are not sure when or how the code attacked into their software.
Read Details
In the last few years as we have adopted the digital form of payments, UPI fraud has surged exponentially accounting for the latest cyber-fraud incidents. Over the last two years, UPI-based transactions have increased four-fold both in volume and value along with an increase in the number of frauds. The best way to get rid of such traps is not to download third-party apps for purpose of complaints; should not reply to or click unverified links sent by unknown persons/banks/companies through WhatsApp/SMS; and should never share sensitive banking information such as UPI PIN, debit/credit card number, CVV, etc. to anyone.
Read Details
Chinese hackers are utilizing VLC Media Player to spy on people secretly. VLC is a very popular media player used by most people. A state-sponsored Chinese group called Cicada or APT10 is using VLC Media Player on Windows PCs to start malware for spying on the government, legal, religious, telecom, pharmaceutical and non-governmental organizations (NGOs) in countries across the globe. This kind of attack on the pre-defined victims, deploying various tools and also observing the target pattern of Cicada’s past activity, clearly indicates that this campaign is espionage.
Read Details
It was noticed that two attempts of cyberattack targeting the electricity distribution in the Union Territory were made by the hackers but they failed to do any harm. The Indian defence system has been strengthened more to counter future cyber-attacks.
Read Details
The security vendor’s appliance was hacked from a confirmation bypass issue. Cybersecurity trusty Sophos has built up a critical vulnerability in its firewall product, which could permit remote code execution. A unanimous independent researcher was credited with reporting the flaw via Sophos’ bug bounty.
Read Details
RBI launched UPI for non-smartphone users named UPI 123 Pay. RBI's 'UPI 123PAY' is an excellent initiative to bridge the digital gap and support the penetration of digital services among low-income groups. It will also encourage higher volumes of digital transactions mostly across rural sectors of the country, which will eventually connect the India-Bharat digital gap and help the nation to move towards a cashless economy.
Read Details
The Russian government appears to have stationed a digital drawbridge to protect websites, the Ukrainian government has issued a call to arms among local hackers, and so-called hacktivists have claimed credit for knocking the website of Russia. Ukraine's Computer Emergency Response Team (CERT-UA) has witnessed a threat from Belarusian state-sponsored hackers targeting military personnel and related individuals as part of a phishing campaign rising among Russia's military invasion of the country.
Read Details
The fraudsters are spoofing LinkedIn accounts to target 'Open to Work' job hunters, who are also being preyed on by huge data-cringing bot attacks.
Read Details
The Union government today has decided to ban 54 apps of Chinese origin in India owing to a national "security threat"; after the continuing border tension. The most liked name "Garena Free Fire - Illuminate" which is an admired alternative to PUBG mobile is onthe list.
Read Details
Two different powerful android trojans named Medusa and Flubot have partnered together to attack android users simultaneously. They have the same specification as spyware and RAT (remote access Trojan) capabilities. The most targeted industry is banking and financial institute those who use apps.
Read Details
Recognizing the work and contribution in the field of forensic sciences, Dr J M Vyas the Vice-Chancellor of National Forensic Sciences University (NFSU) was honoured with Padma Shri, the fourth-highest civilian award in India.
Read Details
Since the trials of the Covid-19 Vaccines by various countries there has been many folds of mystery wrapping up on the aspect of fraudulently created on the name of Vaccine Injections and its implementations. Apart from a lot of hustle and bustle India could achieve a 100 crore vaccination landmark with the support and efforts of its citizens.
Read Details
According to NCRB, there was a steep rise in cyber crime in the last quarter. To keep a check on financial crimes, pesky calls and fraudulent activities, the Department of Telecommunications (DoT) issued an order of deactivating extra sim cards in and across the Indian Subcontinent.
Read Details
Corrupt practices of selling the virtual security arms and ammunitions at a different price to different agencies revealed by the whistleblowers. Read the complete article to know more about the scam exposure.
Read Details
The twitter accounts of Indian Medical Association (IMA), Indian Council of World Affairs (ICFWA) and Mann Deshi Mahila Bank were hacked on sunday night, with them renamed as one the greatest personality Elon Musk.
Read Details
Fraud Cyber Crime Complaint Website has been caught by Delhi Police. The gang used the website to cheat the victims of Cybercrime to take money in the pretext of resolving the case.
Read Details
India's critical Infrastructure like Gas, Water, Electricity as well as Security Installations is at serious risk according to a Bangalore based Cyber Security Company. Serious Vulnerabilities have been brought into notice of the authorities to fix the loopholes. The flaws have made the previously thought cyber-attacks more helpless and susceptible to the industrial belts.
Read Details
The Supreme Court of India on Wednesday gives it's final verdict against the allegations that were used on the Israeli Spyware Company Pegasus. A bench of Justice headed by Chief Justice N.V. Ramana has stated that 'It is absolutely unethical and illegal to keep a track of personal cell phones from remote places without the permission of the concerned.'
Read Details
A massive crackdown against the illegal Indian telecalling industry has been chalked out to scrape out the fraudulent activities that include the cheating of US Citizens from India.
Read Details
The Central Government of India has now set guidelines for the electronic power sector in India to prevent cyber attacks. This step is believed to provide an ample benefit to the power industry and its various bodies. Read More to find out the lawful articles set in the framework.
Read Details
Kharagpur; 7 October, 2021: Delhi Police's Cyber Cell North District has arrested B-tech student of IIT Kharagpur in charge of Cyber Stalking and Morphing Nude Images of almost 50 minor girls.
Read Details
Suspense builds along the database security of the most celebrated Social Media platforms Facebook, Instagram, WhatsApp. Read more to find if your data is safe or compromised.
Read Details
Kolkata; 04 October, 2021: Social Media operations of Facebook, Instagram and Whatsapp server down for 6 hours without any prior notice to the users losing almost 7 Billion USD.
Read Details
Are you a victim of Cyber Crime? Do you know that reporting a cyber crime online through portal is as easy as ABC and also assures the chance of justice. You just need to have few simple documents with you to lodge a cyber fraud complaint.
Read Details
Whatsapp decides to make its cloud chat backup end-to-end encrypted. This step is being counted as a giant leap to look forward to user's privacy while holding the authority from tracking down the cases fraudulent.
Read Details
Instagram is one of the most used social media tools in the 21st century. Instagram has active accounts of almost 200 million which is in turn becomes a strong database for the blackhat hackers. The Dark We Trap on Instagram is spreading it's reach. Are you Safe?
Read Details
The pandemic situation and the practice of Work-from-Home has taken a heavy toll on the safety of the Cyber World. The numbers of crime in Cyber Security has drastically increased leading to compromise various information and data. Find out the rate of cyber crime increase in the last quarter.
Read Details
The term Cybercrime is the most fledging affair of concern as it is constantly making its graph steeper day-by-day. A recent survey by a credible source has come up with an interesting report which states that “Telegram” has been the most preferred destination for the cyber criminals.
Read Details
It was September, 2008 when terrorists from Lashkar-e-Taiba reached the port of Mumbai from Pakistan to lay siege to the city for the next 60 hours. With immediate mayhem, the City of Dreams shook by continuous blasts at the prominent point of Taj Hotels.
Read Details
Aren't you risking your credit or debit card details every time you put it on websites for online payments? How easy would it have been if a secret code provided to you could help you pay conveniently?
Read Details
A serious update came from Microsoft on Thursday warning thousands of clients using cloud computing services. Likewise, renowned companies all around the world were informed about the vulnerabilities. As stated by the cyber security experts, the hackers could have completely accessed the information to read, modify and even remove the database.
Read Details
Though concepts like SMS Header are not at all new when it comes to blast advertisement. SMS Header is basically an advertisement SMS created by a brand or a company with a unique combination of six characters that represent the particular brand or company. These SMSs reach a number of people at a time and help in boosting up a marketing strategy for the brand.
Read Details
The Virtual Private Network (VPN) is the most buzzed word when it comes to the usage of internet communication along with various organizations and its Work-from-Home systems. A dedicated tunnel of network that ensures the best possible security of data packets from the encoder to the decoder.
Read Details
India has become the new favorite for digital hackers. As reported by Check Point Research (CPR), in the last 6 months, the number of cyber attacks in India has tremendously grown. On an average, every week more than 1700 cyber attack cases have been encountered by Indian organizations.
Read Details
User security has been a key concern for many IT companies and other services. It was found that with the help of mobile apps, companies were accessing consumers' location and other information without their knowledge. Now, Google is coming with strict actions on this policy and have developed transparent app policies for developers.
Read Details
As we know, actor Shabana Azim got trapped by online hackers last month, which she also mentioned in her Twitter account awaring other people. Now, these hackers have been caught by the Maharashtra cyber police with the help of 26 graduates (the team also includes some IIT students).
Read Details
It was shocking to find that the official website of Indore police has been hacked, and that the hackers have put anti-Indian slogans out there. Not only "Pakistan Zindabad", but the hackers also used slogans like "Free Kashmir". The hackers have replaced the name and photos of the Indore Police official with these slogans.
Read Details
With the rising hacking activities on Instagram, the platform is waging with a new security alert in the app, that enables the users to keep their accounts updated and secure. This will include the info about the profile settings.
Read Details
A student from Ahmedabad who just passed higher secondary education is caught by local police for a cyber crime. The individual has used 25000 foreign individuals' data to steal money from their bank accounts.
Read Details
In a report submitted to National Technical Research Organization (NTRO) by Gujarat Police's Ahmedabad Cyber Cell confirmed technical bugs in 50 Indian government websites. These are serious flaws which need immediate attention.
Read Details
There is a lot that people have suffered from the last 1-2 years due to COVID. The whole world is struggling and there is nothing that we can think of, instead of hoping for the good days. Amidst the global pandemic, organizations and enterprises are going through the hard cyber security phase.
Read Details
Earlier this year, Apple has introduced the App Tracking Transparency (ATT), which allows users to have an extra layer of security in terms of using the iOS apps. That means, third-party marketers won't be able to track users’ location without their consent; a truly constructive feature of the Apple users.
Read Details
It is suspected that the famous russain cybercriminal group is behind the latest ransom attack, demanding 70 million US dollars and responsible for the 200 companies data leak in the US. The news came just weeks after the US President asked Russian government to take measures against cybercrimes.
Read Details
On 17th June 2021, Thursday, Quick Heal Technologies Ltd. has discovered Joker malware-laced mobile apps on Google Play Store, with around 50,000 downloads. The spy utilizes users' data by linking them to ads and subscribing them to premium services without users’ consent.
Read Details
Our readers are well aware of phishing attacks which are generic and mostly operated by emails; to steal users' information or spread malware in the system. Similarly, vishing attacks are the advanced version of phishing attacks, but over the phone or a voice call.
Read Details
As we all know that Indian government and Social Media Companies are not having a good time in recent times. There was news of Twitter ban, Facebook limitations and much more. So, what's the update?
Read Details
The country is struggling from the second wave of covid-19 virus, and hackers are continuously attacking people with various cyber strains. Hackers are using the sentiment and baiting the public in the name of the PM covid relief fund. Similarly this time, attackers are targeting people under the picture of medicines and donations.
Read Details
Microsoft's security team has recently found a trojan malware attack that hackers are using to target users; the offenders are using pdf file attachments to lure them. Basically, users receive malicious pdf files in emails and when downloaded, a trojan named StrRAT enters into their system. It is a java-based remote access.
Read Details
According to reports by Bleeping Computer, Bose- the audio equipment company has confirmed the ransom attack, and possibly it has exposed some of the employees' data. Besides, an official complaint has been made by the company to New Hampshire's Office of Attorney General.
Read Details
As reported by Wall Street Journal, Google has collaborated with HCA, a hospital chain in the US to track patient data and build healthcare algorithms.
Read Details
WhatsApp vs Govt of India Vs Lawsuit – An open discussion on Zee24Ghanta LIVE on 26th May 2021 at 8pm. Let us have some more insight.
Read Details
As many of the readers don't know, Colonial Pipeline is the largest pipeline system for refined oil products in the US. As reported, "Darkside", a cybercrime hacking group hacked into Colonial Pipeline systems and demanded ransom.
Read Details
Earlier this year, we all heard about the Whatsapp privacy policy controversy. According to the new policy, Whatsapp would be sharing users’ data with Facebook i.e. its parent company. Moreover, users’ denying accepting the new policy will have to quit the popular text messaging app.
Read Details
Cyber security agency has been alerted to be aware of the malicious and fake covid19 vaccine SMS. The agency has also stated that it makes entry into users’ android phones. Also, if a user opens the link or downloads that particular application, he might have to compromise his contact list in circulation.
Read Details
The world is still fighting against the global pandemic and people are worried about their lives. People were eagerly waiting for the vaccination; however, they are still found positive even having the complete doses of the vaccination.
Read Details
The data breach has become one of the most challenging issues in the world these days. Not only the giant organizations but even the common person’s cell phone is not safe. As per the data by Statista.com, the total number of data breach cases reported in the United States was more than 1000 in the year 2020.
Read Details
We are moving towards the end of the first half of 2021, and the world has already experienced so many cyber attacks this year. Each day, we get updates of cyber threats and data breach faced by the different companies and industries.
Read Details
Hackers are targeting the social messaging app using malware, "ToxicEye" a Remote Access Trojan. The trojan will assist the hackers to access users' computers and control them. The reports have been confirmed by Check Point Software Technologies researchers.
Read Details
Things are not going pretty well for Big Basket. The company has already faced a hacking attack in November, and now again the online grocery company has encountered a cyber attack. The hacking group "Shiny Hunters" has leaked around 20 million Big Basket user data and made it available on Dark Web for free.
Read Details
It is tough for any IT company to prevent themselves from modern cyber criminals. Technology pays equal importance to organizations and the digital criminals. SImilarly, Apple, the international brand has come across a powerful cyber attack.
Read Details
WhatsApp Pink is a new virus being spread through WhatsApp groups. It disguises itself as an APK file that promises to download and install a Pink-coloured WhatsApp on the victim's phone.
Read Details
Domino's India is a popular pizza outlet in India and the brand has lakhs of trusted clients throughout the country. According to an Israel cyber security firm, the pizza making company is alleged to be a victim of a cyber attack.
Read Details
Pfizer CEO has come up with an important message that people who have taken the second pfizer corona vaccine dose, need to take the 3rd dose within 12 months. The announcement was made during a panel discussion hosted by CVS.
Read Details
Those who are passionate about video games are very familiar with "cheat code hacking", it's been beneficial when the playing becomes tough. These codes are being extensively used by gamers to enhance their performance; they have been noticed to be as popular among the cyber-criminal.
Read Details
As reported by Cyber News, 500 million users' data is accessed and put on sale on the internet. The stolen data includes Names, Email ids, Work information and Links to various social media accounts. The data is available for sale on a popular hacker's platform.
Read Details
Upstox is one of the leading stock broking firms in India. It ranks second after Zerodha, in terms of active users. The firm is connected with 2.5 million clients, and it is expected that their data has been leaked online. This could be the biggest KYC leak in the country.
Read Details
Humans have become so lustful that anyone can fool them by offering fake free offers. Recently, an app named "FlixOnline" was found with similar intentions. People have widely advertised the app on WhatsApp informing that the app is giving 2 months free Netflix subscription; that can be used anywhere in the world.
Read Details
In a recent major Facebook data breach case, around 533 million people’s details are alleged to be leaked on the net. According to the sources, the data is expected from about 100 countries, and the data is available for free online on the low-level hacking forums. The Facebook leaked data contains Names, Gender, Relationship Status, Occupation and Work details (date of joining, company name and others).
Read Details
The network slicing supports a specific mobile operator to split their network into several virtual blocks that offer multiple traffic resources. It is actually a logical block present in the 5G core network, allotted to private networks, machine to machine communication, automatic, streamlining, or a mobile virtual network operator
Read Details
Recently, some unknown offenders added a backdoor in the source code of the official PHP Git server. The incident has put the websites at risk of complete takeover using tained code. The open-source server codes were used to build websites.
Read Details
This is the largest ransom attack to date. Acer, the popular computer brand, was hit by a ransomware attack recently, to which the hackers have demanded USD 50 millions.
Read Details
Cybercriminals leave no space when it comes to frauds. Indeed, the crisis works as an opportunity for them. Similarly, as the world is a bit relaxed due to the release of the awaited COVID-19 vaccine, the cybercriminals have some other plans.
Read Details
As we know that WhatsApp caters End-to-End encryption for its messages and communication used on the platform. That means, whatever we share on the channel is private between the sender and the recipient. Hence, the security is inviolable, and it is near to impossible to steal the shared information.
Read Details
As described by the US government, five hacking groups are targeting Microsoft email servers. Out of these 5 groups, one is alleged to be from China.
Read Details
A huge power cut was observed by the public in Mumbai city. The trains were impacted and even the stock market was closed. Hospitals were running on back-up generators. All these happened at the coronavirus outbreak; which made the situation even challenging.
Read Details
Organisations have always invested in perimeter security as the endpoint was supposed to be in the trusted zone. Now with employees working from anywhere and everywhere, companies will invest a lot on endpoint security, as well as the authentication and authorisation tools and techniques. VPN, privileged access management, etc. will be the key technology.
Read Details
A big update has come from the Reserve Bank of India, the apex financial institution of India that online merchants and shopping platforms are not allowed to store the debit/credit card information of the users.
Read Details
The demand and popularity of cryptocurrency have led black hat hackers to get their hands on it. The illegal activists are using their computing power to mine Bitcoins. As per reports, the hackers have already started with their strategies.
Read DetailsYour movement on the internet is not secured anymore with 'Favicons'. Let's know about Supercookies - the tracking method.
Read Details
This is really important. If you are among the others who use Gmail, LinkedIn, Hotmail, and Netflix, you certainly need to read it carefully.
Read Details
Hundreds of Instagram accounts were put down by the popular social media app last Thursday. All these accounts were alleged of hacking and selling usernames. The action was taken after the company along with other social media services (including Twitter and Tiktok) investigated OGUsers; a community for digital buyers and sellers.
Read Details
Google says North Korean hackers backed by the government sought cyber research and are into stealing the same. Let's know more about it.
Read Details
Millions of devices are exposed to unethical hackers due to a serious DNA bug. People's data are at high risk now. Let's know more about it.
Read Details
Do WhatsApp chats serve the purpose as legal evidence? Let's know further how admissible WhatsApp chats are in the court of law in India.
Read Details
The battle cry of privacy is everywhere. This time, one of the most popular and widely used apps WhatsApp is under scrutiny due to its new privacy policy.
Read Details
We have entered the new year, and everyone is looking for a positive-going year— we all have waited for 2021. However, for some people, the bad luck continues.
Read Details
Cybercriminals are rapidly turning their way to India. After the recent JusPay data breach confirmation, another 3 Indian companies got exploited by the black hat hackers. It is expected that around 1.3 crore users' data were breached from these companies.
Read Details
Yes, we are talking about our favourite messenger app, "WhatsApp". The application is so popular and needful that every smartphone user has it on their device. The disagreement started among the users as the company issued their updated terms and privacy policies.
Read Details
Shockingly, around half a million employees' credentials were breached and put on sale at Dark Web. As per reports of KELA, a threat intelligence agency, the data comprises employees of top 25 gaming firms. The gaming industry is on the top list of these illegal activists who harvest and sell confidential data at Dark Web.
Read Details
Do you know how Amazon and Swiggy process their payments on their platform, and is it really safe?
Read Details
Adobe has officially announced the shutdown of Adobe Flash Player and requested users to stop using it. Besides, the organisation advised people to avoid any third party website or application to download the same, as it can put them at risk.
Read Details
A global ad phishing campaign has been detected by cyber security researchers. Over 6.15 lakh Facebook user accounts across 50 countries have been compromised via exploiting the pages of GitHub.
Read Details
As confirmed by Mr. Rajeev Chandrasekhar - a BJP MP, the Joint Parliamentary Committee (JPC) has redrawn the Data Protection Bill. Mr. Rajeev Chandrasekhar confirmed the announcement at the Global Technology Summit 2020 event organized by Carnegie India.
Read Details
Online scams are rapidly growing in India. Scammers are getting clever and using different strategies to put people into their trap. Moreover, these illegal activists have entered into our smartphones without our knowledge - they are not limited to the email inbox.
Read Details
It'll cover 24 of the most recent ransomware attacks (so far) in 2020 - what they were and who they impacted - as well as some of the latest news and trends in ransomware attacks.
Read Details
As we all know that Google services like YouTube, Gmail, Docs, and others faced outrage on Monday, 14th December 2020. All these services were down for around 45 minutes. The outrage impacted users all around the globe.
Read Details
Yesterday, millions of Gmail users experienced a server down across the globe. For around an hour, Gmail, YouTube, Google Assistant, and Google Docs were out of service after being hit with a widespread outage (502 Error).
Read Details
CERT-IN (Indian Computer Emergency Response Team) has warned internet users in India about major security vulnerability in the Chrome browser. This is one of the biggest chrome updates issued by Google.
Read Details
Microsoft is always concerned about the security of its users. The company timely releases the Tuesday patches to keep their system strong and flawless. Likewise, Microsoft releases fixes for 58 new security vulnerabilities for 11 of its products and services.
Read Details
Bumble is one of the popular dating sites used globally. With the growing popularity, it has also set up interest among cybercriminals. Recently, security vulnerability has been noticed in the platform which could lead to data risks for around 100 million users.
Read Details
Cybercriminals, posing as social media or SEO assistants, tricked millions of Facebook users. Firstly, they ask the victims to provide their Facebook credentials via a tool that will show who visits their Facebook profiles.
Read Details
In July 2020, the Government of India banned 43 Chinese apps with one massive stroke of restriction. Many believe it was an act of retaliation for the brutal killing of our twenty soldiers in the Galwan valley by the Chinese soldiers. Well, that is not the only reason. The decision deals with a huge range of threats that these apps inflicted on our society as well as national security.
Read Details
Google is a search engine and provides various internet amenities to its users for advancement and betterment (Gmail, Google Maps, Google Drive, and many others). The renowned organizations never entertain hackers or any malicious activities. Google is a symbol of trust for corporate.
Read Details
BigBasket is an emerging online platform in India helping consumers to buy daily household goods at attractive discounts. Recently, it was found that the exciting platform falls in a controversy of a data breach of its consumers' information, which was sold on the Dark web.
Read Details
Google project zero has observed security vulnerability and reported the same in just 7 days. The bug identified as CVE-2020-17087, a Windows Kernel Cryptography Drive bug, exploited for privilege escalation such as sandbox escape.
Read Details
The flaws were found in the FontParser and kernel which were rolled out in various devices (Pad, macOS, iOS and watchOS). The vulnerability benefits the adversaries with arbitrary codes and executes the malware at the kernel-level.
Read Details
Recently, people have found excessive spam messages in their gaming chatbox. People from all around the globe have been irritated by this attack. Generally, they were getting random messages to subscribe to a YouTube channel named Eric Loris.
Read Details
Mithaas, one of the renowned sweets sellers in India, has recently been trapped by ransom attackers. As per Mithaas Sweets management, the computer servers were hacked which results in 5 years of data loss.
Read Details
PTI (Press Trust of India) computer servers have experienced an immense ransom attack. The attacks lead to an interruption in their operation and delay in delivering news to their Indian subscribers. Moreover, it took an all-night endeavor by the engineers to restore it.
Read Details
Recently, Microsoft has found 2 serious remote code Windows vulnerabilities which could majorly affect the Windows Codecs Library and Visual Studio Code. Fortunately, the patches were quickly detected and resolved, before it could make an impact on the system.
Read Details
Do not hand it over to anyone at a restaurant or petrol pump. Ask to swipe in front of your eyes. Ask to bring the POS in front of you. Do not allow the guy to go out of your sight taking away your debit card. He can take photos of both sides of the debit card and use it on ecommerce sites without OTP or PIN.
Read Details
The Insurance Regulatory and Development Authority of India (IRDAI) is an autonomous body dealing with regulating and promoting the insurance industry in India. It is true to say that it controls the insurance companies in the country.
Read Details
As reported, around 50,000 home cameras are claimed to be hacked by an unknown hacking group. Moreover, cybercriminals have stolen the video clips and pictures, and uploaded some of it on the internet.
Read Details
Microsoft has alerted its users about the new mobile phone ransomware attack. The ransomware takes advantage of the incoming call notifications and the android home button to get stored behind the locked screen.
Read Details
A team of five security researchers has worked and monitored the Apple online security services for 3 months (July to September), and found a total of 55 flaws. Out of these 55 flaws, 11 vulnerabilities are indicated as severe critical.
Read Details
The University Grant Commission (UGC) has issued an updated report stating the names of the fake universities running in the country. The list reveals a total of 24 universities from Delhi, Uttar Pradesh, West Bengal, Odisha and other states.
Read Details
Bollywood actor Pooja Bedi is the latest cyberattack victim in the country. It is reported that a cybercriminal group has threatened to hack her website (www.happysoul.in) and sell drugs on the platform if she denies paying the ransom amount.
Read Details
Yes, it is true. Google Playstore removed Paytm from the platform due to its "Fantasy Game offering", on Friday, 18th September.
Read Details
DisrupTor, a result of the cyber operation conducted by the international security agencies against the Dark Web vendors and buyers. As a result, 179 Dark Web vendors were arrested across the US and Europe. These vendors are alleged of selling illegal items on the Dark Web platform.
Read Details
The coronavirus has been proved as a threat to technology and online businesses. It has affected many enterprises— many of which have also reached the shutdown point. Start-ups and medium scale businesses have found it hard to survive amidst COVID-19.
Read Details
According to various intelligence sources, it is being said that Alibaba, the trusted wholesale chinese marketplace is stealing data of Indian people. Around 72 India based servers are alleged in the data breach, sending the information to China.
Read Details
The US government has reported charges against 5 cyber criminals supported by the Chinese States. Along with the 5 members, 2 Malaysian hackers are also included in the list. As per the investigation, these criminals have accessed around 100 companies worldwide.
Read Details
CISA (Cybersecurity and Infrastructure Security Agency) has reported that from the past one year, chinese cyber criminals are scanning US government network devices. The security agency has released an alert informing about the cyber group which is meant to be connected with China's Ministry of State Security (MSS).
Read Details
If you are running an online store e-commerce business, then this post is for you. This is a lesson for us - Why it is so important to perform regular updates on our e-commerce sites!
Read Details
As per reports, it is confirmed that around 10,000 renowned Indians are under the watch of China. The data includes politicians, sportspersons, actors, businesspersons, judiciary and journalists. The Chinese government is monitoring these individuals and organizations closely in their database.
Read Details
Team TMT cyber criminal group is back with their unique strategy to attack the cloud infrastructure. This time, they have used a legal way to reach their mischief desire.
Read Details
The Acronis Cyber Readiness Report 2020 has put out a serious concern for Indian companies. The report ranked India as the top victims of the cyber attacks, compared to the other developed nations amidst COVID-19. The companies have also mentioned that their IT costs have immensely grown in the last few months (almost double) due to the cyber attacks.
Read Details
Railway Protection Force (RPF) Patna, has uncovered some essential points from a ticket broker who has hacked the IRCTC website to book tickets. The RPF took the individual into custody on Monday and got some crucial information from him.
Read Details
The Prime Minister's personal website's Twitter account (@narendramodi_in) had been hacked by a hacker named John Wick. Several tweets have been taken down which were urging people to donate in the PM Relief Fund, a recently created fund against the backdrop of COVID - 19 crisis, in cryptocurrency.
Read Details
The former Chief Security Officer of Uber, Joe Sullivan has been charged for covering a massive data breach in 2016. They paid $100000 to hackers for keeping the incident secret. The recent press release of the U.S. Dept. of Justice states "Sullivan took deliberate steps to conceal, deflect, and mislead the Federal Trade Commission about the breach."
Read Details
If you are a Microsoft operating system user, it is intrinsic to know that recently, the organization discovered two unrevealed security risks namely: CVE-2020-1530 and CVE-2020-1537. With an immediate effect, Microsoft announced an emergency update for Window 8.1, Window RT 8.1 and Server 2012 R2.
Read Details
Qbot (a banking trojan that steals bank account credentials and financial information). This time, it's mainly targeting the military, government, and manufacturing sectors.
Read Details
Security researchers have found some low-cost Chinese smart phones ship with malware that aims to steal your money. The low-cost Techno W2 smartphone has shipped with a malware that subscribes to paid services to steal the user's money. The budget smartphone sells in African countries like Egypt, Ghana, and South Africa along with Indonesia and Myanmar.
Read Details
When it comes to cloud storage, be it saving personal information, confidential company details or sensitive data, people rely on Google Drive greatly.
Read Details
Maharashtra cyber, the state's nodal cyber security agency recently issued an advisory against a "WhatsApp hijack fraud" targeting users.
Read Details
In this year August 20 on Thursday the Gmail suffered massive outrage worldwide with many users complaining that they could not send any attachments or documents while the other few reported that they have not been able to log in at all. Popular outrage tracking portal down detector has reported that user reports indicate Google is having problems since 1:16 AM EDT.
Read Details
The largest cruise line in the world has been hit by a ransomware attack, with customer data also believed to have been accessed. Carnival corporation which operates more than 100 vessels across 10 different brands that include Carnival Cruise Line, Princess Cruises, and Costa cruises with over 150,000 employees and 13 milion guests annually notified the U.S. Securities and exchange commission(SEC) this week after detecting the attack on 15th August where the threat actors accessed and encrypted a portion of one brand's information technology systems. They also downloaded files from the company's network.
Read Details
Team of academic has detailed this week vulnerability in the voice LTE (VOLTE) protocol that can be used to break the encryption on 4g voice calls. Today in present a new attack called REVOLTE that could let remote attackers break encryption used by voice calls and spy on targeted phone calls.
Read Details
On 14 august 2020, a Chinese national with his three Indian associates have been arrested in a crackdown on an illegal gambling racket. After launching into the allegations money laundering against different Chinese nationals and their associate based on India by the income tax department. The alleged gambling was organised by different companies under umbrella of China based firm called BejingT Power Company.
Read Details
User records of UberEats, an American online food ordering service, have been leaked by a threat actor.
On Dark Web, a Cyber security firm came across the data after its dark web and deep monitoring. UberEats is an American online food order and dispatch service that was launched by Uber in 2014.
Read Details
In the month of July U.S travel management firm CWT paid $4.5 million this week to the hackers' stolen reams of sensitive corporate files and said they had knocked 30,000 computers offline, according to a record of the ransom negotiations seen by Reuters. The attackers used a strain ransomware called Ragnar locker, which encrypts computer files and renders them unusable until the victim pays to be restored.
Read Details
In today a Twitter user leaked a report that 20GB worth of confidential Intel documents stored on file sharing service documents that the twitter users claimed they received from an unknown hacker. According to the leaker, the folder contains classified information under NDA, and the hacker who provided the documents to the leaker said they had obtained the files earlier this year. The files have been posted publicly anywhere before the hackers are supposed to prepare to release more Intel data.
Read Details
In the previous month there was a bitcoin and crypto currency attack using top high profile men. The biggest security breach with accounts of former US president Barack Obama, US presidential nominee Joe Biden, Tesla founder Elon Musk, Musician Kayne West and Apple among others, hacked and used to post links to bitcoin scam. Once the accounts have been taken over, the hackers then send requests so that if bitcoin were sent to the accounts they would be doubled and returned.
Read Details
One of the most dangerous is that cybercriminals are exploiting the retails giant's prime now service, where customers can get items like games consoles. Recently, AARP recounted several scams where cybercriminals posed Amazon's customer service or security team as a ploy to steal your personal information. Security experts have raised serious concerns about how easy it is for fraudsters to hack into Amazon accounts.
Read Details
Recently cybercriminals are getting active because during this pandemic situation all the country are following lockdown so the people are doing work from home so the people are busy using social media platform and hackers are getting stealthier and findings new ways of remain undetected and hijacking accounts for long period of time stealing the vital information and sending spam mails to different e-mail id's.
Read Details
Today the government has banned 47 more Chinese apps in India. In the previous month more than 58 Chinese apps were banned by the government to protect our country from national interest and security including most popular apps like TikTok.
Read Details
Cyber Revenge in simpler words a vengeance sought online. The concept of cyber revenge has become one of the greatest threats to commoners in recent times. It is the distribution of sexually explicit image or video of individuals without their consent. More vividly it has led to the defamination of young girls and women in general. The doctored photos are being uploaded, followed by numerous monetary frauds, cyber revenge ranks second in number of registered cases while in some states. Cyber Revenge crimes top in list. Read the article to know more about the menace and possible solutions.
Read Details
In these pandemic situations the hackers are more active and try to hack as many servers as possible. A few days early we saw that several high profiles were hacked in Twitter.
Read Details
A new threat discovered by security researchers PayPal, Gmail, Netflix, Amazon, Twitter, Facebook and TikTok are just a few of the hugely popular apps targeted by the latest Android malware but fortunately, it's pretty to stay safe.
Read Details
India & Israel have signed an agreement expand collaboration in dealing with cyberthreats rapid increased in digitisation due to coronavirus situation that exposed the vulnerabilities of the virtual world.
Read Details
"MADE IN CHINA". A very common sentence in every Indian's life, but aren't we ignorant enough to not realize how we are slowly dependent on it. Does it not strike a lighting when we talk about self-dependence, this word should equally applicable to the things we use in our daily life. Indians are considered to be the most brilliant minds around globe.
Read Details
On 15th July 2020, a wide range of celebrity & brand accounts started tweeting out a message promoting a crypto giveaway in which funds sent to a specified bitcoin wallet would send back double the amount of the user and in social media platform this attack is one of the biggest cyber attacks in history.
Read Details
Even a dormant or inactive domain can turn bad and begin pointing to partner program pages, phishing sites, or even malware. According to Kaspersky, researchers found about 100 websites for sale on one of the world's biggest auction platforms, and these sites redirect visitors to over 2500 unexpected & unwanted URLs.
Read Details
In a recent development, Google removed the Remove China Apps from the Google Play Store. This came into effect immediately after Google removed India's Mitron app, the so-called rival of the Tiktok app from China. The incident of these removals from the Play Store was first noticed by Indian Express.
Read Details
The popularity of the Mitron app has been phenomenal as more than 5 million users downloaded it in their Smartphones since it got launched. The experts believe that is India's reply to the popular Chinese app Tiktok. However, the app development professionals believe that Mitron App has some vulnerabilities that need to be fixed before it reaches further users.
Read Details
As reported by ZDNet, the latest attack is a very serious one, as it's able to target users of facebook with personal details & credentials stolen by hackers from our social network account.
Read Details
Recently Kaspersky researches say that users can safeguard themselves by turning off the automatic adding of invites to our Google calendar app.
Read Details
TikTok has been found to be stealing information from your iPhone, which can include banking transactions, passwords and confidential files. With so many celebrities using TikTok, find out how vulnerable you are.
Read Details
Allowing to work from home is a very good option at the present situation, but it has some difficulties in the aspect of proper computer system, network security, consistent power supply, high speed internet, code and software piracy, PCI DSS compliance, etc. Are we moving more towards WFH, or is this a hype which is bound to fail.
Read Details
An Indian entertainment giant ZEE5 faced a serious threat in June 2020, when a self-declared group of hackers 'Korean Hackers' or 'John Wick' claimed to have hacked the huge databases of ZEE5.
Read Details
A major scam or security breach has been detected by the Meerut Police officials in Uttar Pradesh. They have found more than 13,000 (13,557 to be more precise) Vivo handsets running with the same International Mobile Equipment Identity (IMEI).
Read Details
It happened when the government decides to ban the WeTransfer website in India. According to a news report appearing in Mumbai Mirror, the instructions have been put into force with immediate effect. WeTransfer has been a popular file-sharing website that was fairly popular among Indian users. As per a report, the website allowed transferring huge files with anyone without having a paid account.
Read Details
In a drastic decision, Google has removed more than 813 creepware apps from the official Android Play Store. This step comes only after Google received research reports from a group of academics that were busy in their work to find the activities and impact of Creepware.
Read Details
Responding to the privacy concerns by renowned tech experts in the country, Niti Aayog, in a landmark move, has open-sourced the code of Arogya Setu App, an app developed by the Government Of India to track and monitor the happenings related to Covid-19 pandemic.
Read Details
Hacked! User data of more than 4.75 crore of Indian professionals have been compromised yet another time. This time, the hacker targeted the data from Truecaller, one of the most popular data service providers in India and abroad.
Read Details
India is experiencing the fourth instalment of the national lockdown to combat corona virus from Monday, 18thMay 2020. It has been nearly two months that we been masked and marooned on our individual islands executing our personal and professional duties in equal measure.
Read Details
Computers installed with Intel's Thunderbolt ports are vulnerable to hands-on hacking attempts due to security issues in its hardware interface, according to research by BjörnRuytenberg, a security researcher at Eindhoven University of Technology in The Netherlands.
Read Details
A cyber security researcher Matthew Bryant has released a Chrome extension called 'CursedChrome' that can turn the Chrome browser into a hacker's proxy bot. Though, there is another tool to avoid active attacks through such extensions.
Read Details
If you have a Samsung Galaxy Phone with versions from 2014, then you may have a reason to worry. This happens mainly because of Samsung's acceptance of a massive security threat that all Galaxy Mobile phones are likely to encounter, that were manufactured and marketed after 2014.
Read Details
The world is changing fast, especially due to the recent pandemic COVID-19. The leading organizations plan to leave China for their role in the spread of the pandemic. Till now, quite a few organizations have declared their move to Taiwan and it is here that the incident has hit.
Read Details
The news of data theft at Unacademy has struck the world with wonder as well as uncertainty. The news piece said that the academy faced a major setback when the hackers took away the database of more than 22 million users that the academy used to manage.
Read Details
Salt is a powerful Python-based automation and remote execution engine which allows users to issue commands to multiple machines directly.
Read Details
As federal entities of UK, USA and Australia are engaged in socio-political spat over the pros and cons of end to end encryption, Whatsapp, which was a strong supporter of the same, has been fuelled by two back to back security enhancers lately, which is all set to affect its massive user base worldwide.
Read Details
According to the SITE Intelligence Group, which checks online extremism and terrorist activities, anonymous activists have exposed nearly 25,000 email addresses and passwords allegedly belonging to the National Institutes of Health, the World Health Organization, the Gates Foundation and other groups working towards global abolishing of COVID-19.
Read Details
The United States agencies have released a joint advisory reminding the world about the 'significant cyber threat' posed by North Korean state-sponsored hackers to the global banking and financial institutions.
Read Details
Zoom is the new doom for the netizens, thanks to the spread of the COVID-19 virus all over the world.
Read Details
The year 2019 has witnessed more number of cyber attacks using Zero-Day vulnerabilities than its 3 preceding years.
Read Details
According to a report from Malwarebytes, web skimming attacks have increased by 26 percent in March alone compared to previous months.
Read Details
Recently cyber security researchers have discovered an IoT botnet threat that leverages corrupted smart devices to stage 'distributed denial-of-service' attacks, potentially triggered on-demand through platforms offering DDoS-for-hire services.
Read Details
Traffic meant for more than 200 of the world's largest content delivery networks (CDNs) and cloud hosting providers has been siphoned by Rostelecom, Russia's state-owned telecommunications provider.
Read Details
Just clicking on a website, malicious or otherwise, unknowingly loading malicious ads using Safari browser could have let remote attackers secretly access your device's camera, microphone or location and in some cases saved passwords as well.
Read Details
A cyber security research team has discovered the "Mandrake" spying operation targeting Australian mobile banking users.
Read Details
As per the findings of cyber security expert @_g0dmode, the Zoom video conferencing software for Windows is exposed to a classic 'UNC path injection' vulnerability that could allow remote attackers to steal victims' Windows login credentials and even execute arbitrary commands on their systems.
Read Details
A renowned name in the international hotel industry the Marriott has fallen prey to a data breach for the second time in quick succession during the last two years.
Read Details
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle.
Read Details
At least 19 popular electronic merchandising websites have been corrupted with a new version of the digital skimmer called 'Make Frame' by a current Magecart skimmer campaign intended at stealing payment card information of the customers.
Read Details
Recent analytical findings from Dr.Web have revealed hackers actively targeting users with a malicious Chrome update which runs s backdoor on the target device which then allows the later malware attacks.
Read Details
With an alarmingly high global population staying put at homes and using virtual communication platforms like 'zoom' to communicate online, the bad actors of the world are making the most of the moment by coming up with phoney platforms to cajole the innocent and the unsuspecting.
Read Details
Third party Android App developers are using Corona virus related keywords in their app names, descriptions, or in the package names in order to delete malware, perpetrate financial theft and rank higher in Google Store searches related to the topic.
Read Details
Hammersmith Medicines Research, the British medical organization that had earlier researched the Ebola vaccine and is now on standby to perform the medical trials on any COVID-19 vaccine has been hit by the cyber crime group in terms of stealing medical reports of those affected by the virus and publishing them online to extort ransom.
Read Details
The global black hat community is out to reap the most of the present worldwide vulnerability by cajoling people into getting infected with malware in the garb of Corona consciousness.
Read Details
Researchers have zeroed down upon immediate remedies of corona affected cyber security issues of working from home on personal computers.
Read Details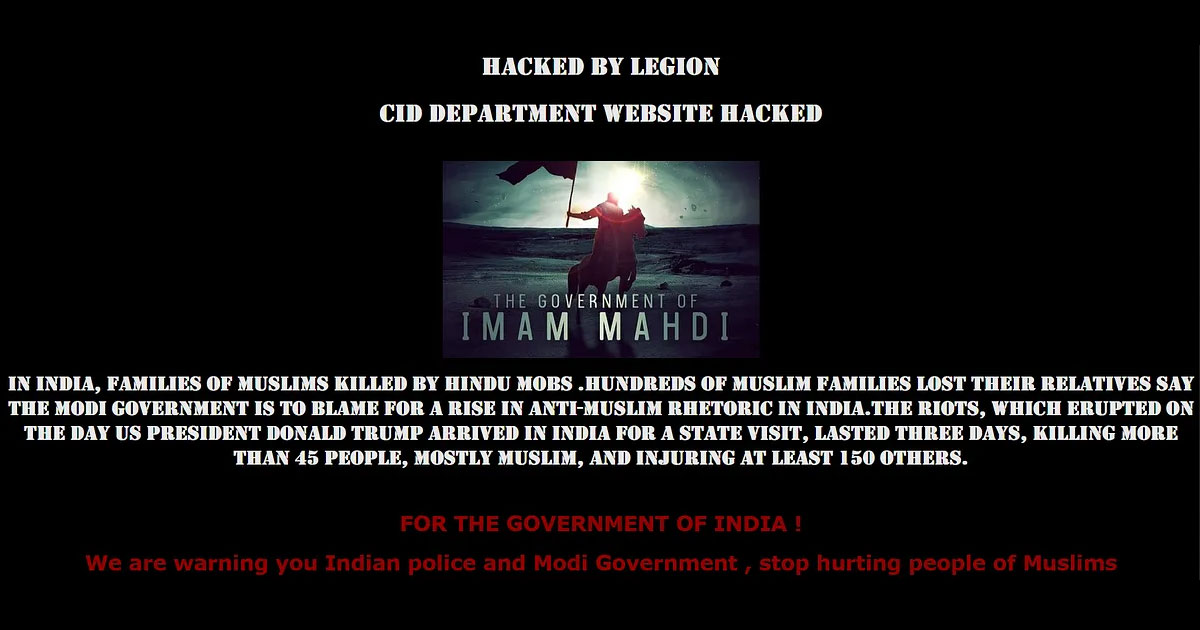
On Friday an Islamic hackers group called Legion hacked the website of Maharashtra CID as payback procedure to the Delhi massacre which caused the death of many Muslims.
Read Details
A new simple yet extremely risky strain of Android malware has been discovered which steals users' authentication cookies from the web browsing and other apps, including Chrome and Facebook, installed on the corrupted devices.
Read Details
The signing entity is having to retrace 3 million TLS certificates issues by default because of avirus in its Certificate Authority software.
Read Details
Clearview AI, the much talked about facial recognition company, has intimated its clients about a critical hacking of its customer database which includes some of the most powerful law enforcement agencies in the United States.
Read Details
Cyber security researchers announced new high-severity hardware vulnerability present in the popular Wi-Fi chips manufactured by Broadcom and Cypress which are activating an array of digital devices including smartphones, tablets, laptops, routers, and IoT gadgets.
Read Details
Google has released a blog post asking mobile app developers to encrypt data that their apps generate on the users' devices, particularly when they use unprotected external storage that's exposed to virtual corruption.
Read Details
