Work from home is the new door for threat actors to barge in.
India is experiencing the fourth instalment of the national lockdown to combat corona virus from Monday, 18thMay 2020.
It has been nearly two months that we been masked and marooned on our individual islands executing our personal and professional duties in equal measure.
Personal chores include cooking and cleaning while its professional counterpart means working from home to make both ends meet.
And there looms the peril.
In order to understand the situation let us shed some light on the term attack surface.
According to the tech book,
The attack surface of a software environment is the sum of the different points (for "attack vectors") where an unauthorized user (the "attacker") can try to enter data to or extract data from an environment. Keeping the attack surface as small as possible is a basic security measure.
Hence, the bigger number of devices connected to a network, the bigger is its attack surface making it easier and accessible for hackers to intrude into the network. In short, each new device is a gateway where hackers can find vulnerabilities in and use it to wreak havoc on the system.
Thus the world wide phenomenon of working from homemakes the cyber space a happy hunting ground for hackers like never before.
Before lockdown employees who worked from home usually worked with special work laptops with enhanced security, under strict guidelines and a separate, secure wi-fi connection.
Here a hacker had to navigate multiple security hoops to even get past the welcome screen. For example, he must plug in a USB security stick to "unlock" work files. These measures make hacking difficult, but not impossible.
But in an emergency situation like this most firms have had little time to arrange for such elaborate security measures for their remote workers. With non- customized work laptopsloaded with confidential personal information and unsecure home internet connection this is field day out for hackers who only need to gain access through one entry point to seize control of a whole network. Once they’re in they can steal data, secrets, and even lock you out of the network.
Let us check out some statistics.
Hackers broke into the networks of America’s largest defence contractor, Lockheed Martin, by targeting remote workers.
In the past couple months; hackers have targeted the US Department of Health.
Attacks against the World Health Organization have more than doubled.
Cyber intelligence firm CYFIRMA revealed cyber threats related to corona virus shot up 600% from February to March. It’s only a matter of time before we hear about a major cyber breach.
And it is also the time for cyber market speculation.
As the attack surface grows bigger and better with more and more people working from home with vulnerable connections, it is time for cyber disasters and stock market speculations. Cyber stock and hacking attacks have a love hate relationship.When major hacks hit the newswire, cyber stocks surge.
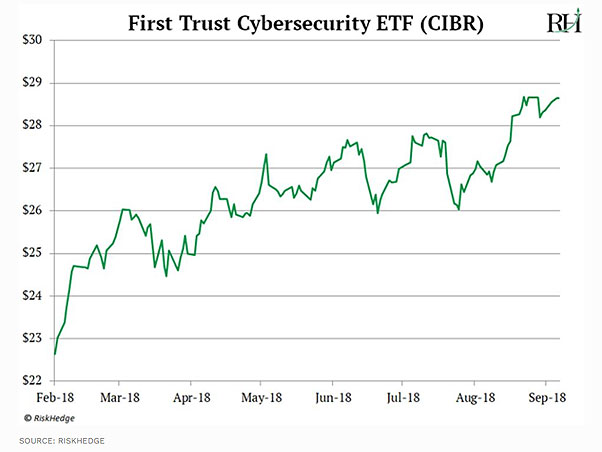
Facebook and Cambridge Analytical scandal made the largest cyber security ETF (CIBR) jump 25% over the next six months.
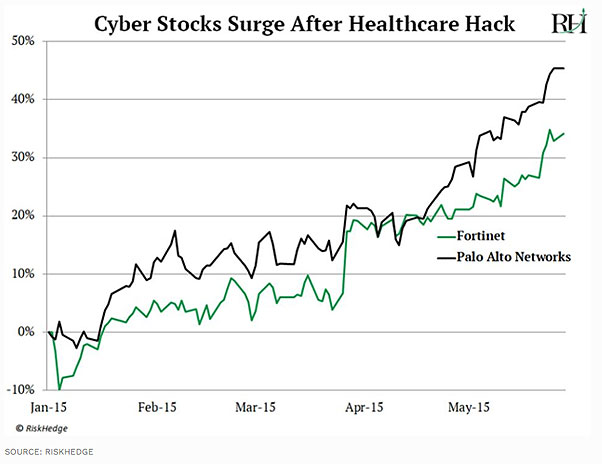
US health insurer Anthem revealed 80-million personal records were stolen. Many cyber stocks jumped 30%+ over the next four months.
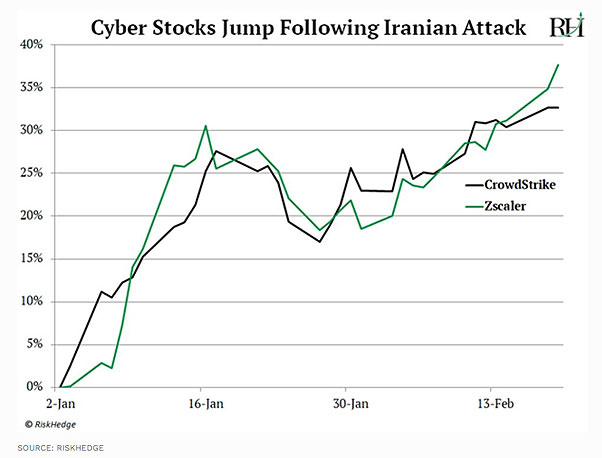
US military launched a missile attack that killed an Iranian general. Iran is a cyber superpower, and they vowed revenge by striking America’s digital networks. Some cyber stocks jumped as much as 30% in just six weeks.
Investors choose to buy cyber stocks after every major cyber attack.
ISOEH leaves no stone unturned to make the cyber enthusiasts able of combating all cyber threats with its updated courses.
Read on for more hacking stories during the pandemic.
Exclusive Blog
Read All Exclusive Blog »
With world working from home, it's time to make it enjoyable and effective.
Read DetailsHacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read Details