
Two different powerful android trojans named Medusa and Flubot have partnered togetherto attack users simultaneously as per ThreatFabric's research. They have the same infrastructure as spyware and RAT (remote access Trojan) capabilities.
What Is FluBot Malware and how it spreads?
FluBot is a very polished type of malware targeting Android users through fraudulent messages or notifications. They create a notification to an individual about a new voicemail or missed call from an unknown number.The message may appear as "You have 1 new Voicemail(s);Click on the [link]."It contains a fake link that divertsusers to a website that looks convincing enough, and it convinces the users to read or listen to what they've missed. Meanwhile, it installs malware into the device.The malware will then ask the user to givepermission to the app. When the user agrees, it gets down to business and starts attacking various apps. FluBot most favorite app to attackis Android users' mobile banking apps.Even iPhone users can receive such messages, but the malware seems to only work on Android phones.FluBot spreads very fast because it uploads contact numbers to a command and control (C&C) server, then it sends messages to each of those numbers. The numbers thenget added to the device's blacklist and it disables the operating system's built-in security, allowing it to cause chaos undetected.
What is Medusa?
According to Greek Mythology, Medusa is described as a winged human female who has hairs of living venomous snake. It is said that those who look into her eyes would turn to stone.She is meant to represent a dangerous threat meant to scare-off other dangerous threats, an image of evil to repel evil.Unlike Flubot, Medusa is now being distributed through the same SMS-phishing infrastructure as Flubot, resulting in high-volume breaches to data leakage. Apparently, Medusa follows the same pattern of attack as Flubot. As per ThreatFabric, "In less than a month, this distribution approach allowed Medusa to reach more than 1,500 infected devices in one botnet. "It has multiple botnets performing multiple campaigns side by side.
In July, 2020 Medusa was first detected in a financial company based in Turkey. After Turkey, mostly targeted countries are North America, Europe, and Canada. It got accessibility permissions in Android to draw funds from banking apps to another account controlled by the attacker. Thus, Medusa mostly targets banking and financial institutes since it has got multiple remote-access features. FluBot (aka Cabassous), has upgraded its' own feature and has the ability to intercept and manipulate notifications from targeted applications on a victim's Android device by leveraging the direct reply action, alongside auto-replying to messages from apps like WhatsApp to spread phishing links in a viral way.
The following figure shows the code that collects the information of the active window going through its nodes:
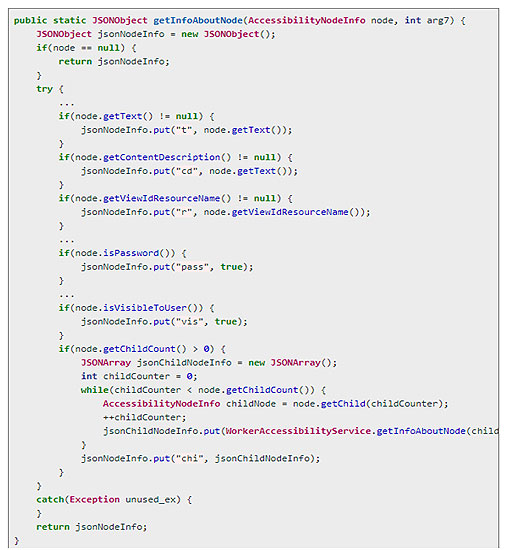
Source: ThreatFabric
At the back-end panel, Medusa tags banking apps with a ‘BANK' tag, to control and edit the input data. This states that any banking and financial institutes over the world are exposed to this threat who has their own app. The command-and-control server (C2) can also command Medusa to carry out many varieties of RAT work.In version 5.4, Medusa hitsthe "Notification Direct Reply" feature of Android OS, which allows the malware to directly reply to push notifications from targeted applications on a victim's device. The user will not be aware of the activity, so Flubot can thus intercept them – opening the door to baffle two-factor authentication and more.
Exclusive Blog
Read All Exclusive Blog »
With world working from home, it's time to make it enjoyable and effective.
Read DetailsHacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read Details









