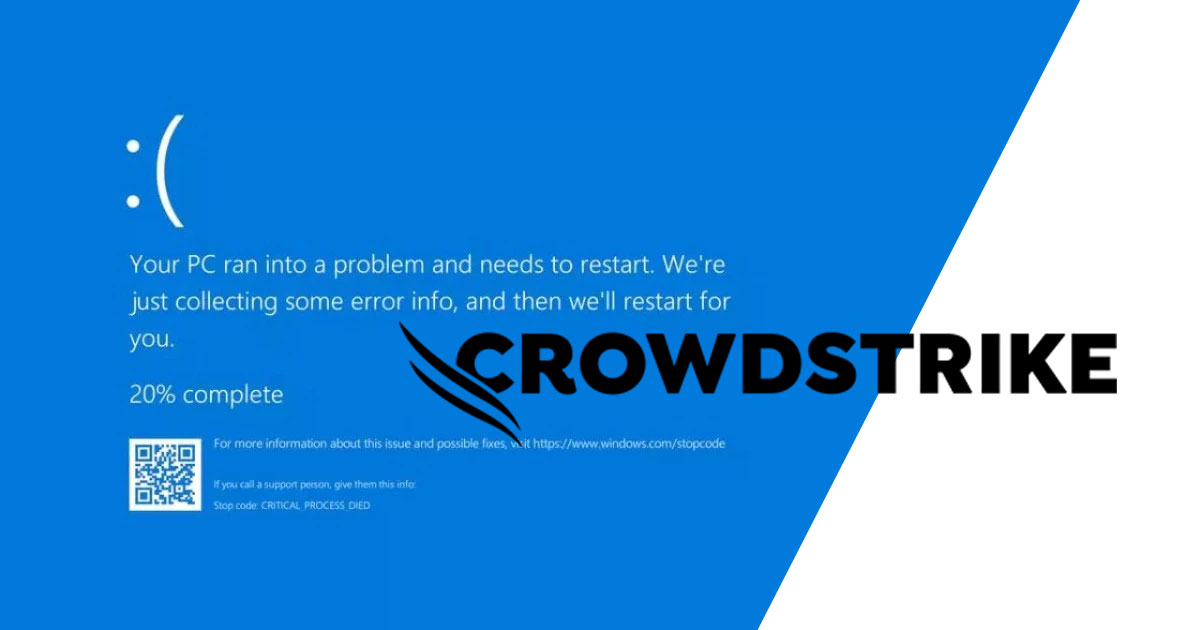
The well-acknowledged cybersecurity firm, CrowdStrike, put forward a detailed Root Cause Analysis (RCA) of the worldwide IT downtime that jolted many enterprises across the globe. The outage of last month served to demonstrate that even the most advanced security infrastructures are inherently flawed, which was felt as tremors in the tech sector.
The Incident Revealed
In the early morning of July 15, 2024, an IT shock struck many businesses across the globe. Initial speculation held that, based on the current state with threats rising, it could have been part of a cyber-attack. But after a thorough investigation by CrowdStrike, the real cause was eventually determined— which painted one of the starkest pictures seen yet in showcasing just how complicated modern cybersecurity issues have become.
Root Cause: The Falcon Sensor Crash
Many businesses use advanced endpoint detection and response technologies by CrowdStrike, like the Falcon sensor, to secure their digital assets. This is what made up the core of the outage. According to the RCA report, a particular misconfiguration within the software of a third-party component is what made the Falcon sensor come crashing down. More specifically, because of this configuration error, it suffered a memory leak that eventually caused the sensor to fail, resulting in a wide-sweeping IT catastrophe.
At this time, the Falcon platform of CrowdStrike, which is designed to provide real-time protection against cyber-attacks, was down. This left many of the companies extremely reliant on CrowdStrike technologies for cybersecurity bare and exposed.
The Ripple Effect
It resulted in a domino effect across several other sectors such as public services, healthcare and banking where uninterrupted IT operations are critical. Many firms reported heavily disrupted daily operations, underscoring the need for ironclad and resilient cybersecurity protection.
However, many people in the industry have complimented CrowdStrike on coming forward quickly and being open about handling the issue. It made a task force right after looking into the core problem and a couple of days later released the RCA report to the public. This action was seen as a proactive step toward maintaining their credibility and trust with their clients.
Detailed Findings from the RCA Report
The RCA study is an in-depth technical discussion of the incident, providing a detailed account of how the misconfiguration crept in and the reasons why it went unnoticed during the initial deployment of the Falcon sensor. According to it, the issue was caused by an inadvertent initiation of a memory leak due to a third-party component upgrade. Such being the reason why this update had not been called out as a potential hazard is that it was a standard maintenance procedure.
The Falcon sensor did crash at the end due to running out of memory available to it which rendered the whole system inoperable. The research also notes that since the sensor is used all across different industries, the problem was exacerbated because of deployment size. The failure of the sensor had global implications because of its very widespread use as a standard.
CrowdStrike's Response and Future Measures
CrowdStrike responded to the outage by putting in place several crucial steps to stop it from happening again. Among them are:
- Enhanced Testing Protocols: CrowdStrike is updating its testing protocols, paying special attention to third-party components, to make sure that such problems don't occur again.
- Improved Monitoring: To find and fix memory leaks and other such vulnerabilities faster, the organization is improving its monitoring capabilities.
- Client Communication: As part of its commitment to keeping lines of communication open with its clients, CrowdStrike will make sure they are made aware of any potential dangers or difficulties as soon as feasible.
- Collaboration with Partners: Given that third-party components had a part in the event, CrowdStrike and its partners are collaborating more closely to enhance the overall integrity of the program.
Industry Reactions
This incident has provoked the cybersecurity community to discuss more widely the reliability of endpoint detection and response systems. While many experts acknowledge CrowdStrike as having top-notch security, this outage is a reminder that even technically advanced problems can happen with the best systems.
Some industry watchers believe that this incident will lead to more stringent controls on third-party software components and a higher bar for cybersecurity solutions. There is a need, now more than ever, to subject every component of software to very rigorous testing and validation before deployment.
Conclusion
CrowdStrike was able to retain its reputation as a cybersecurity leader through a quick response to the global IT outage and by making the RCA report public. Even though the incident exposed some imperfections, it also highlighted the importance of complete transparency and continual improvements within the cybersecurity industry. It is hoped that better controls will be instituted as learning opportunities from this disaster are realized by the industry, which would benefit organizations worldwide.
Exclusive Blog
Read All Exclusive Blog »
With world working from home, it's time to make it enjoyable and effective.
Read DetailsHacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read Details










