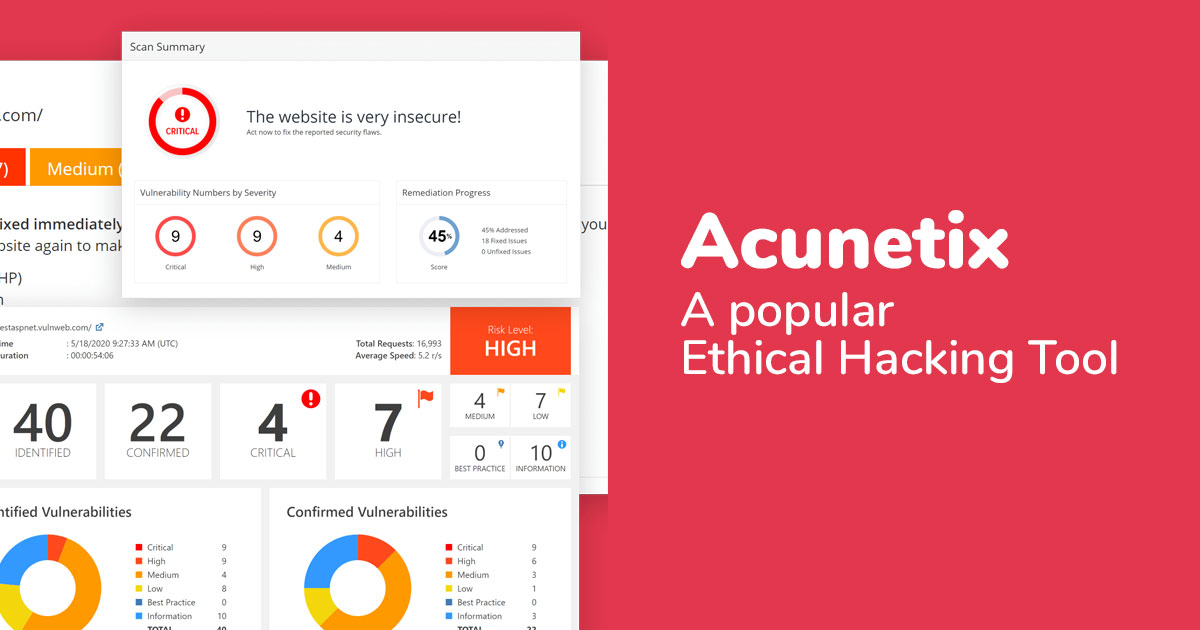
Acunetix is a completely automated ethical hacking tool that helps detecting and reporting almost 4500 and more web applications and its vulnerabilities.
Read Details
It helps to identify and focus on the interesting areas of a huge firmware image. Although Emba is optimized for offline firmware images, it can test both, live systems and extracted images.
Read Details
HackTools, is a web extension facilitating your web application penetration tests, it includes cheat sheets as well as all the tools used during a test such as XSS payloads, Reverse shells and much more.
Read Details
SkyArk deals with the new uprising threat of cloud shadow admins how attackers find and abuse non-trivial and so called limited permissions to still make it through and escalate their privileges and become full cloud admins. Furthermore attackers can easily use those tricky specific permissions to hide stealthy admin entities that will wait them as undercover persistence technique.
Read Details
Burp suite is a set of tools used for penetration testing of web applications. It is developed by the company name Portswigger, which is also of its founder Dafydd Stuttard. Burp suite aims to be an all in one set of tools and its capabilities can be enhanced by installing add on that are called BApps.
Read Details
This is a popular wireless stumbler for MAC OS X offers many of the features of its namesake Kismet, though the base code is entirely different. KisMAC offers a pretty GUI and was around before Kismet was ported to OS X. KisMAC is a wireless network discovery tool for MAC OS X.
Read Details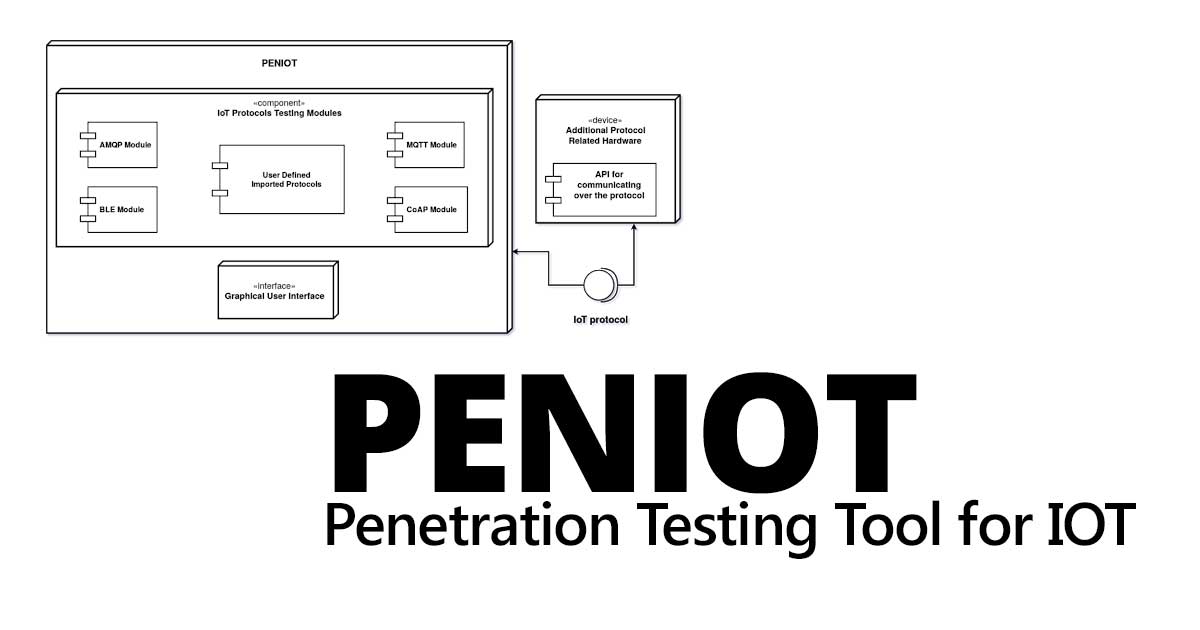
PENIOT is a penetration testing tool for internet of things (IOT) devices. It helps you to penetrate your devices by targeting their internet connectivity with different types of security attacks.
Read Details
Wireshark is open source network protocol analysis software program started by Gerald Combs in 1998. A global organization of network specialists and software developers and support Wireshark and continues to make updates for new network technologies and encryption methods.
Read Details
Kalitorify use iptables settings to create a Transparent Proxy through the Tor Network. It is a bash script to be used for a safe navigation during communications, searches or other activities with Kali Linux, but doesn't guarantee 100% anonymity.
Read Details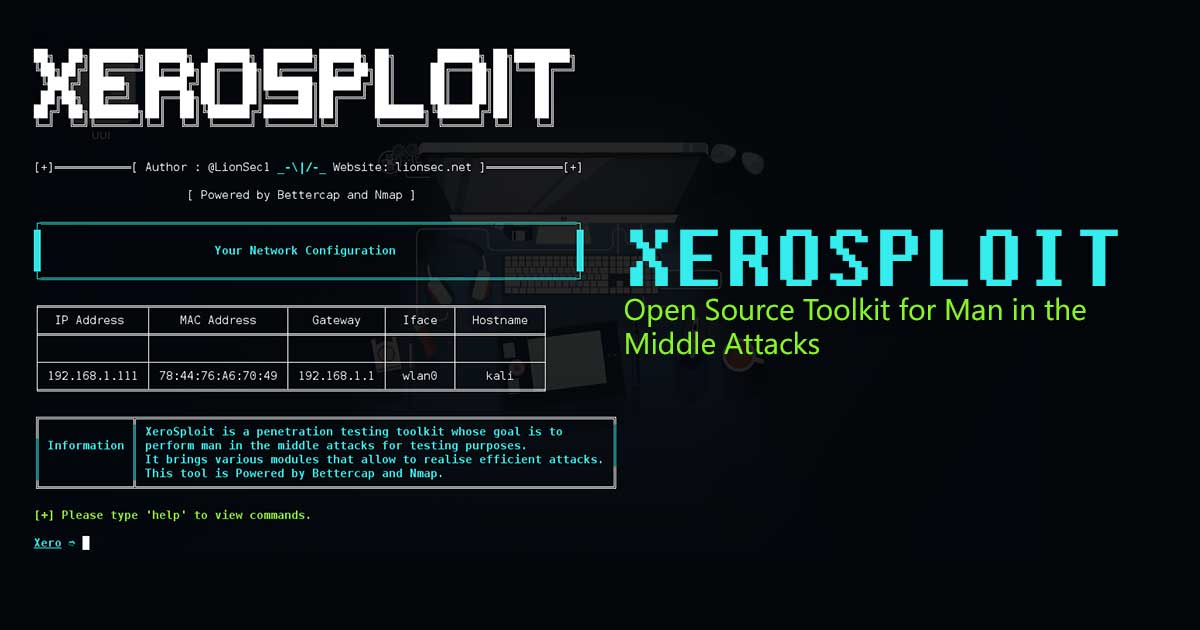
Xerosploit is a penetration testing toolbox whose objective is to perform the man in the middle attacks. A man in the middle attacks is when an attacker intercepts communications between two parties either to secretly modify traffic traveling between the two.
Read Details
The tool generates a malicious HTTPS page using Ngrok Port Forwarding method, and a javascript code to perform cam requests using MediaDevices.getUserMedia.
Read Details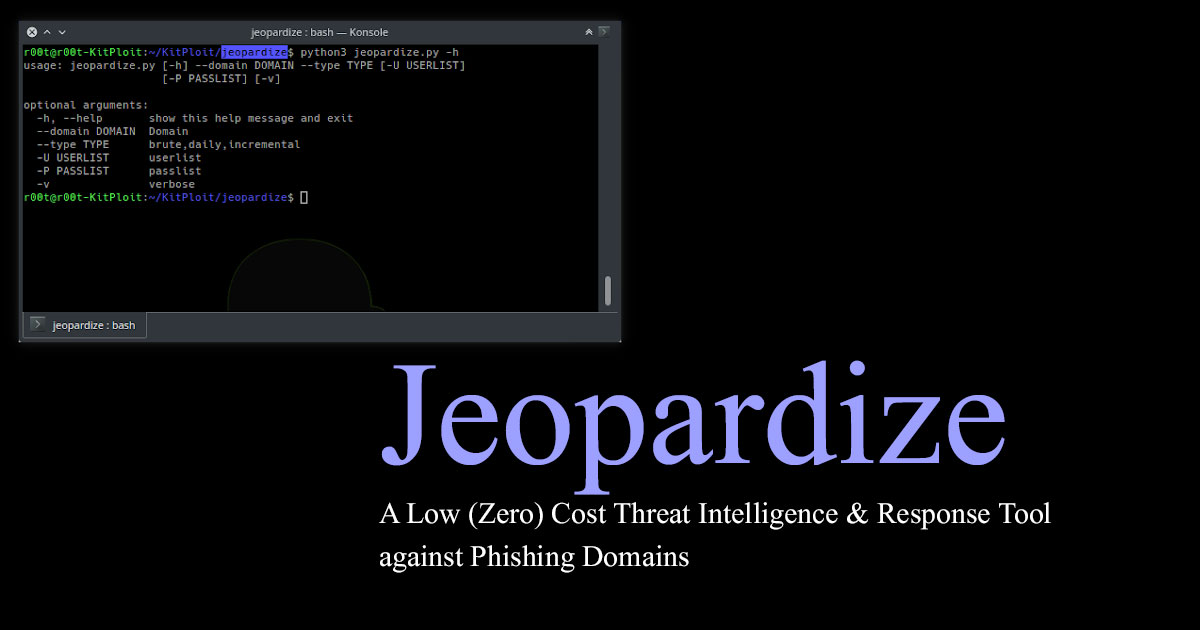
Jeopardize tool is developed to provide basic threat intelligence & response capabilities against phishing domains at the minimum cost as possible.
Read Details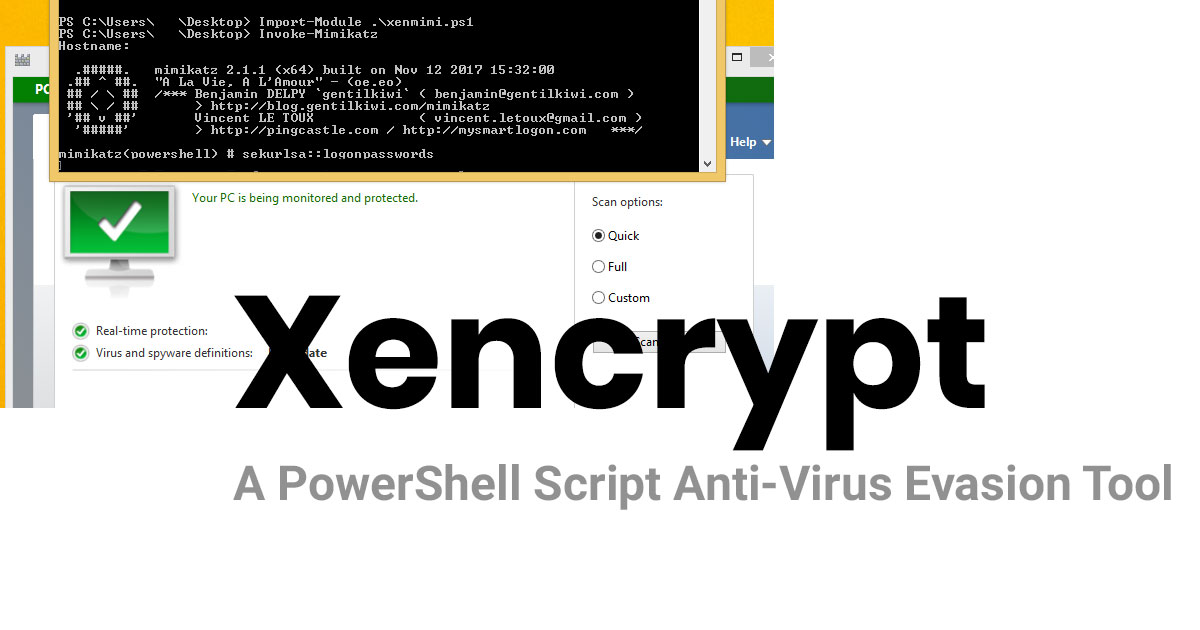
Xencrypt is a PowerShell crypter that uses AES encryption and Gzip/DEFLATE compression to with every invocation generate a completely unique yet functionally equivalent output script given any input script.
Read Details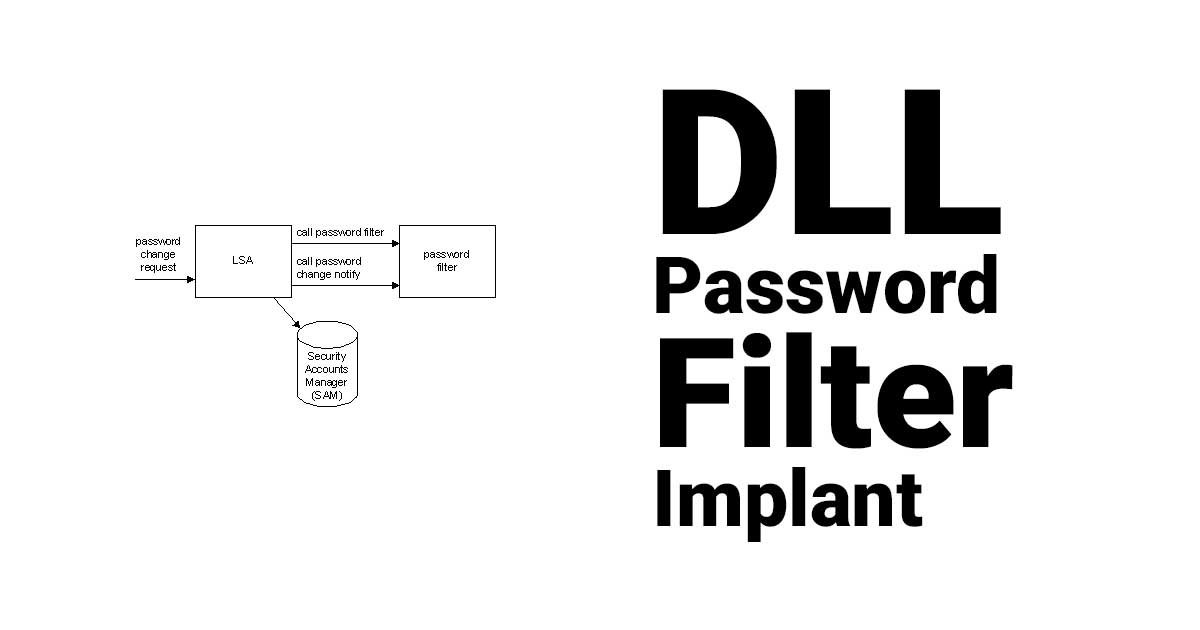
DLLPasswordFilterImplant is a custom password filter DLL that allows the capture of a user's credentials.
Read Details
Kawaii Deauther is a pentest toolkit whose goal is to perform jam on WiFi clients/routers and spam many fake AP for testing purposes.
Read Details
nfstream is a Python package providing fast, flexible, and expressive data structures designed to make working with online or offline network data both easy and intuitive.
Read Details
Qiling is an advanced binary emulation framework. Qiling is backed by Unicorn engine.
Read Details
SCShell is a fileless lateral movement tool that relies on ChangeServiceConfigA to run commands. The beauty of this tool is that it does not perform authentication against SMB. Everything is performed over DCERPC.
Read Details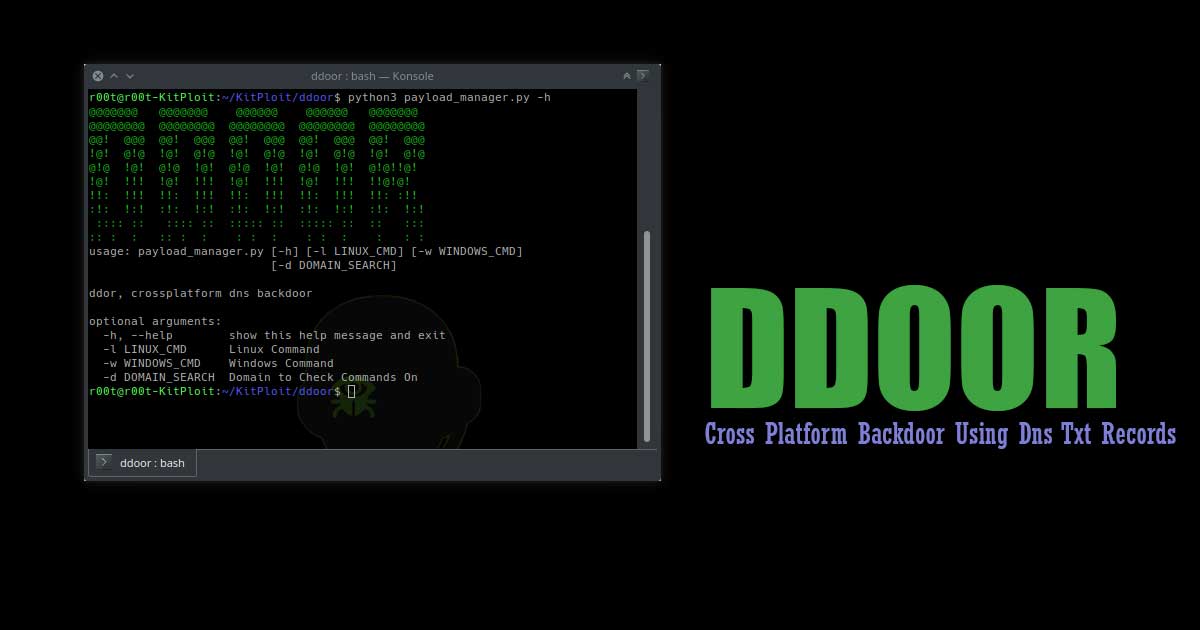
ddor is a cross platform light weight backdoor that uses txt records to execute commands on infected machines.
Read Details
RedPeanut is a small RAT developed in .Net Core 2 and its agent in .Net 3.5 / 4.0. RedPeanut code execution is based on shellcode generated with DonutCS. It is therefore a hybrid, although developed in .Net it does not rely solely on the Assembly Load.
Read Details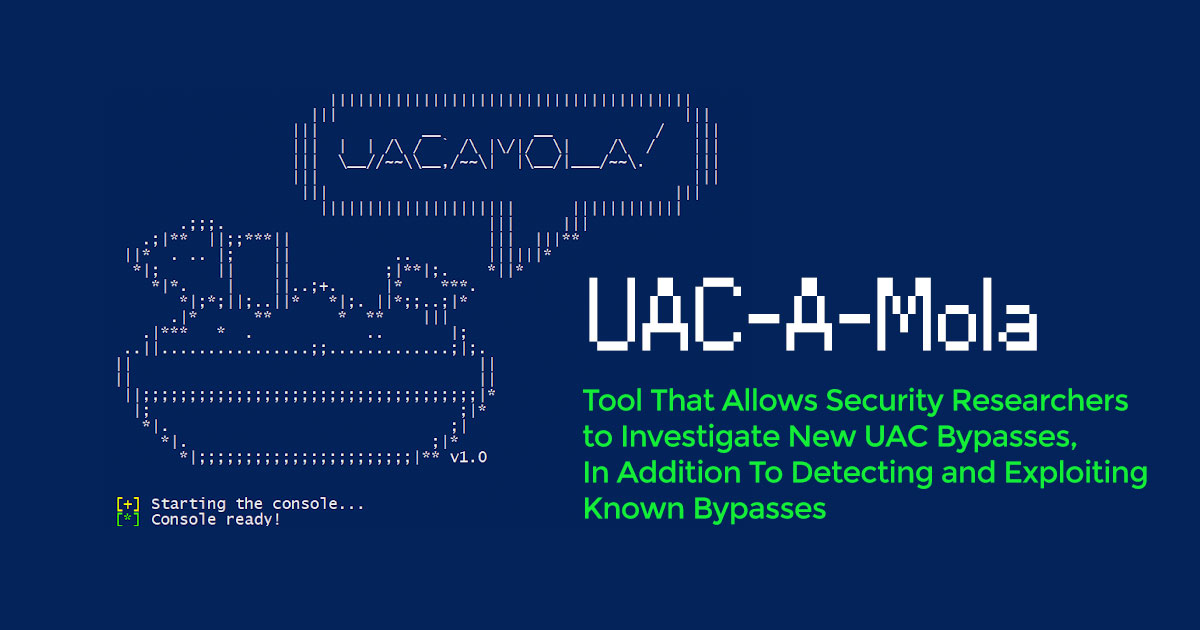
UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting known bypasses. UAC-A-Mola has modules to carry out the protection and mitigation of UAC bypasses.
Read Details
FOCA is a tool used mainly to find metadata and hidden information in the documents it scans. These documents may be on web pages, and can be downloaded and analyzed with FOCA.
Read Details
An XMLRPC brute forcer targeting Wordpress written in Python 3. In the context of xmlrpc brute forcing, it's faster than Hydra and WpScan. It cans brute force 1000 passwords per second.
Read Details
EAPHammer is a toolkit for performing targeted evil twin attacks against WPA2-Enterprise networks. It is designed to be used in full scope wireless assessments and red team engagements.
Read Details
Postenum is a clean, nice and easy tool for basic/advanced privilege escalation vectors/techniques. Postenum tool is intended to be executed locally on a Linux box.
Read Details
SMTP Tester is a python3 tool to test SMTP server for 3 common vulnerabilities.
Read Details
MalConfScan is a Volatility plugin extracts configuration data of known malware. Volatility is an open-source memory forensics framework for incident response and malware analysis.
Read Details
Mosca is a manual static analysis tool written in C designed to find bugs in the code before it is compiled, much like a grep unix command.
Read Details
Pftriage is a tool to help analyze files during malware triage. It allows an analyst to quickly view and extract properties of a file to help during the triage process.
Read Details
ADAPT uses Python to create an automated framework to use industry standard tools, such as OWASP ZAP and Nmap, to perform repeatable, well-designed procedures with anticipated results to create an easly understandable report listing vulnerabilities detected within the web application.
Read Details
Stardox is an advanced github stargazers information gathering tool. It scraps Github for information and display them in list tree view. It can be used for collecting information of your's/someones repository stargazers details.
Read Details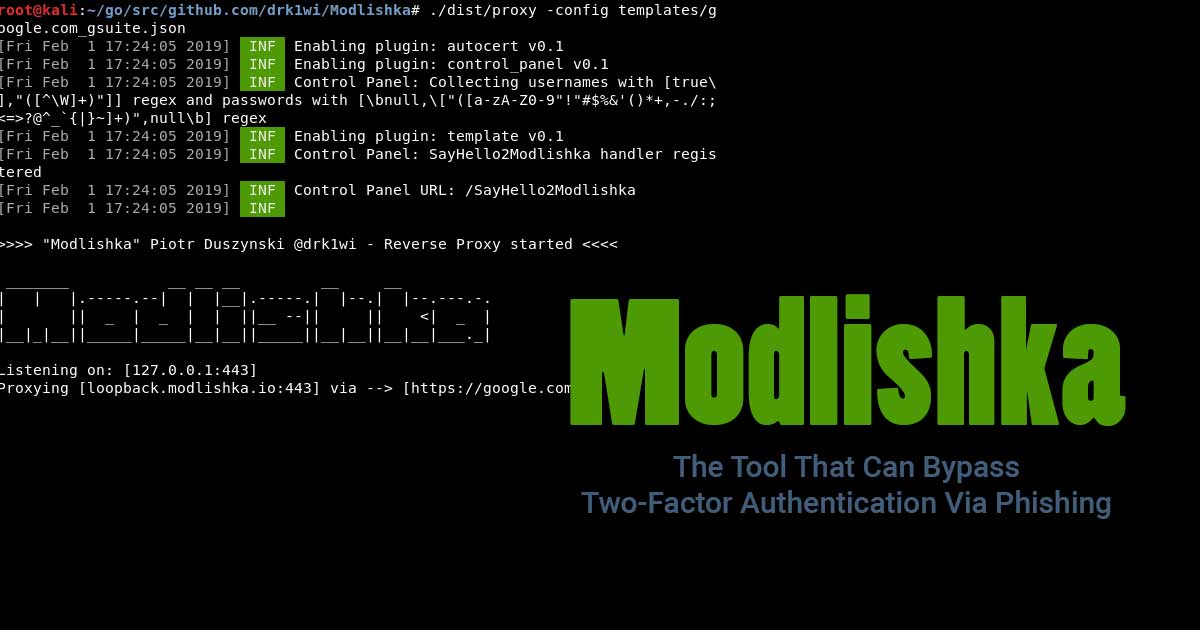
While most users consider two-factor authentication a security measure to protect accounts, a researcher has proved otherwise. The tool can bypass two-factor authentication and automate phishing attacks.
Read Details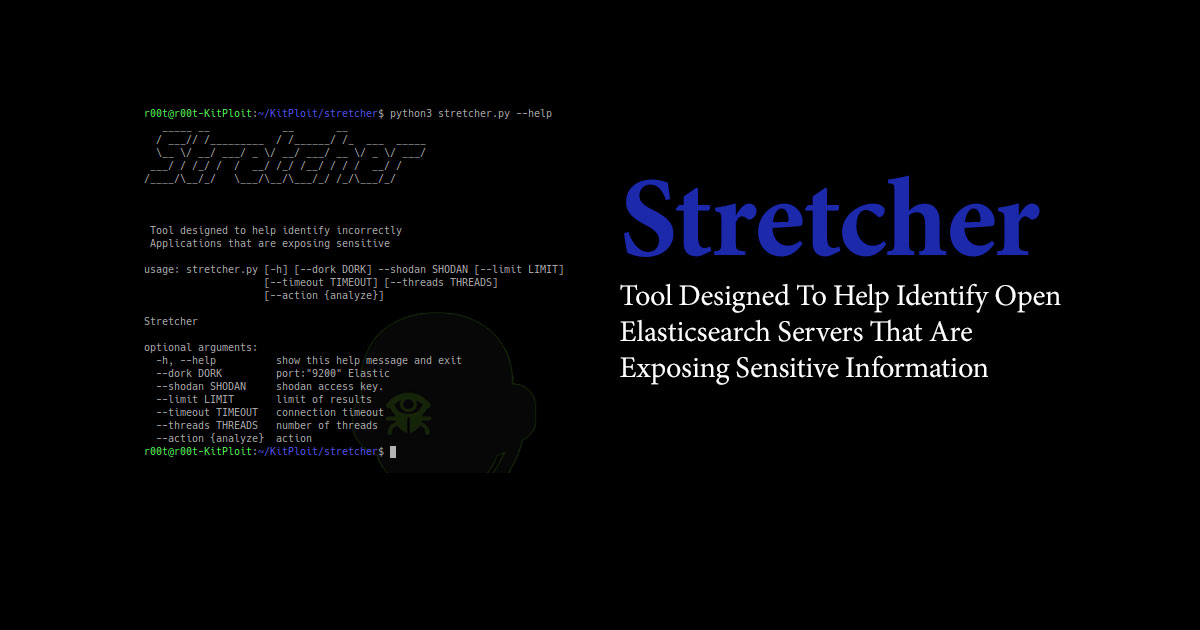
Stretcher is a tool to search for open elasticsearch servers.
Read Details
Brosec is an open source terminal based tool to help all the security professionals generate the right payloads and commands.
Read Details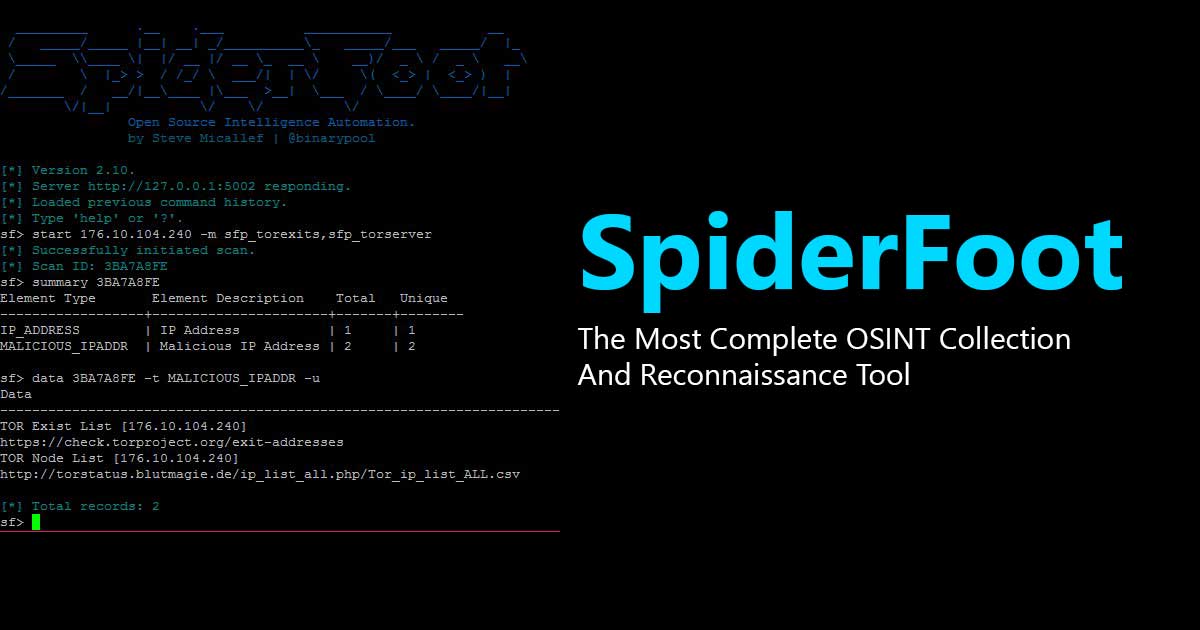
SpiderFoot is a reconnaissance tool that automatically queries over 100 public data sources (OSINT) to gather intelligence on IP addresses, domain names, e-mail addresses, names and more.
Read Details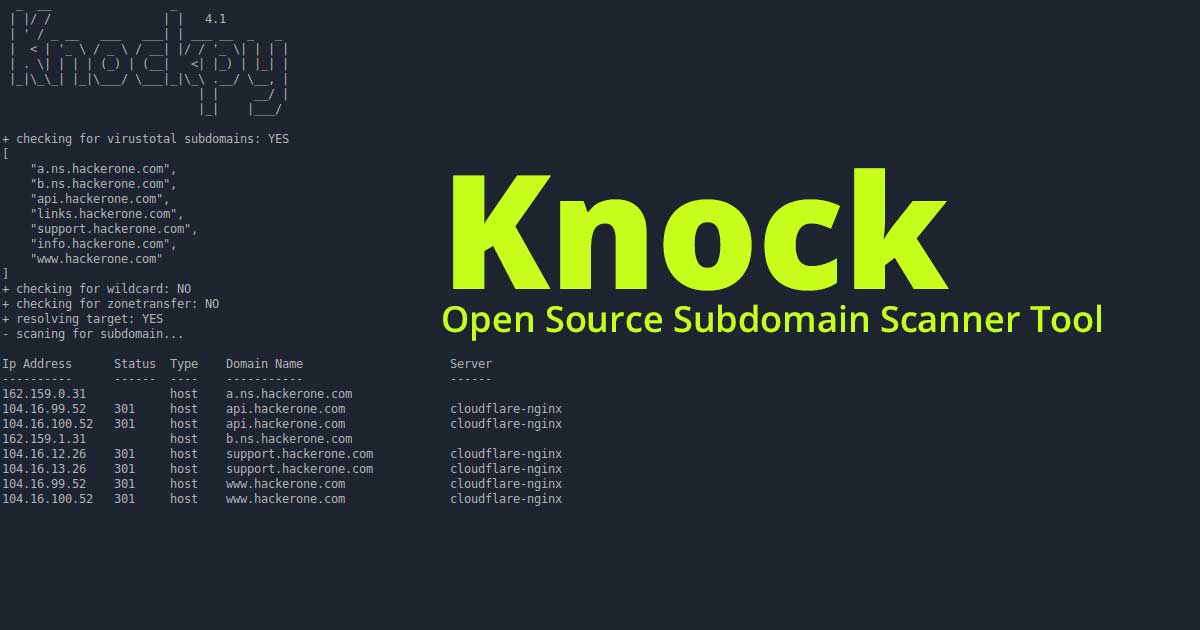
Knock is a python based tool for enumerating subdomains on a targeted domain.
Read Details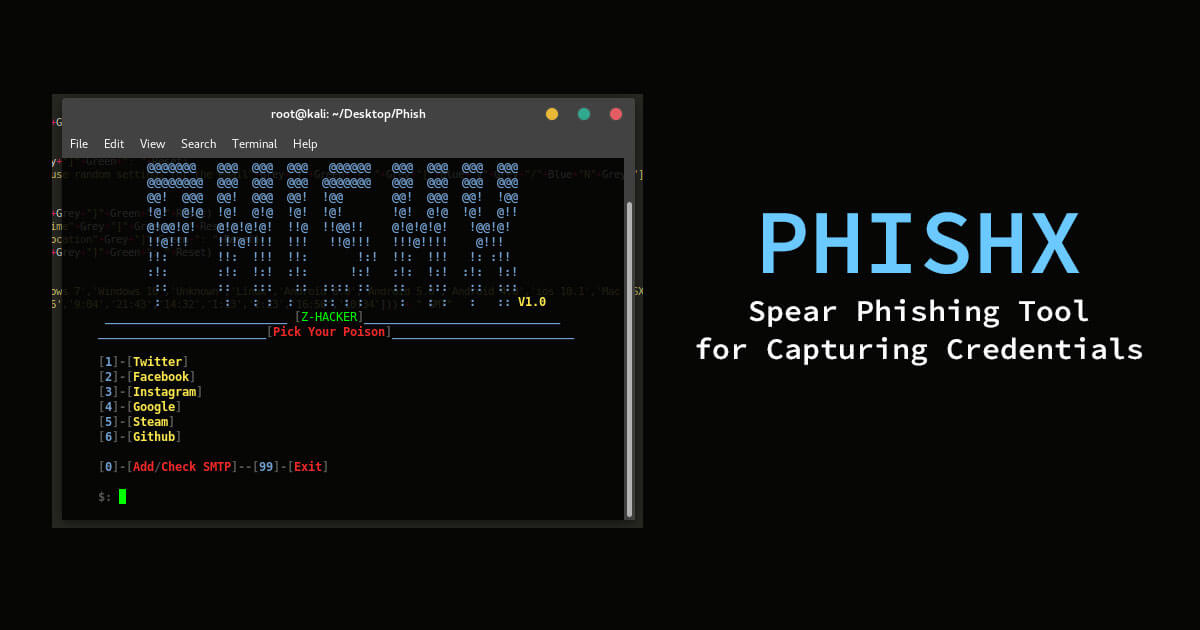
PhishX is a python tool that can capture user credentials using a spear phishing attack.
Read Details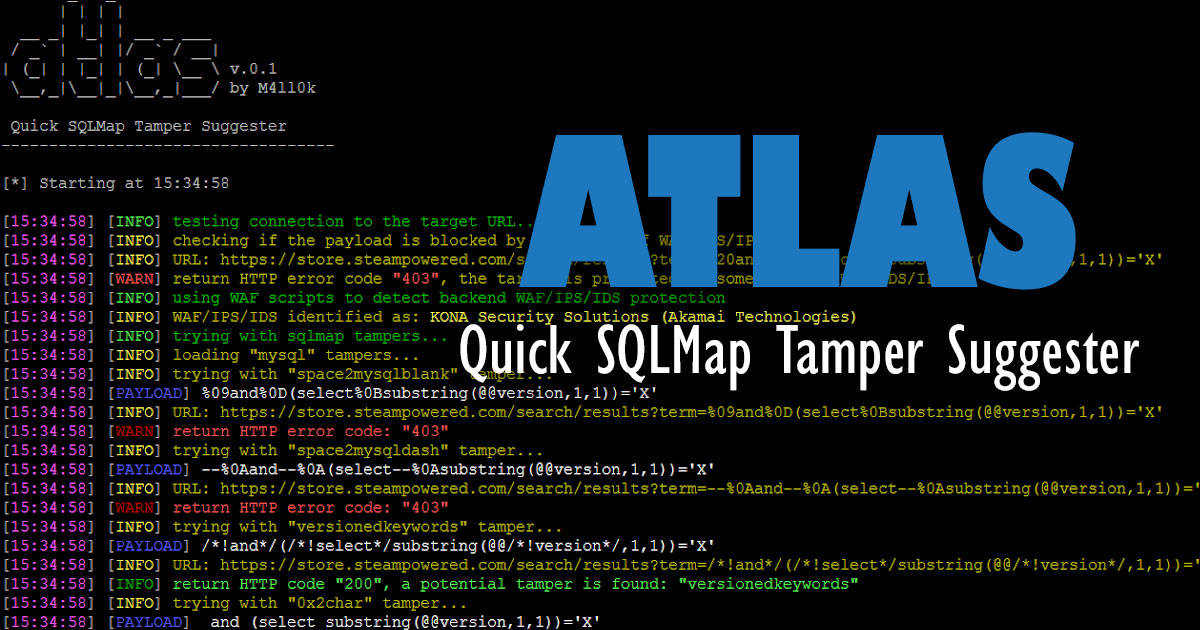
Atlas is an open source tool that can suggest sqlmap tampers to bypass WAF/IDS/IPS, the tool is based on returned status code.
Read Details
XenoScan is a memory scanner which can be used to scan the memory of processes to locate the specific locations of important values.
Read Details
Ettercap is a comprehensive suite for man in the middle attacks.
Read Details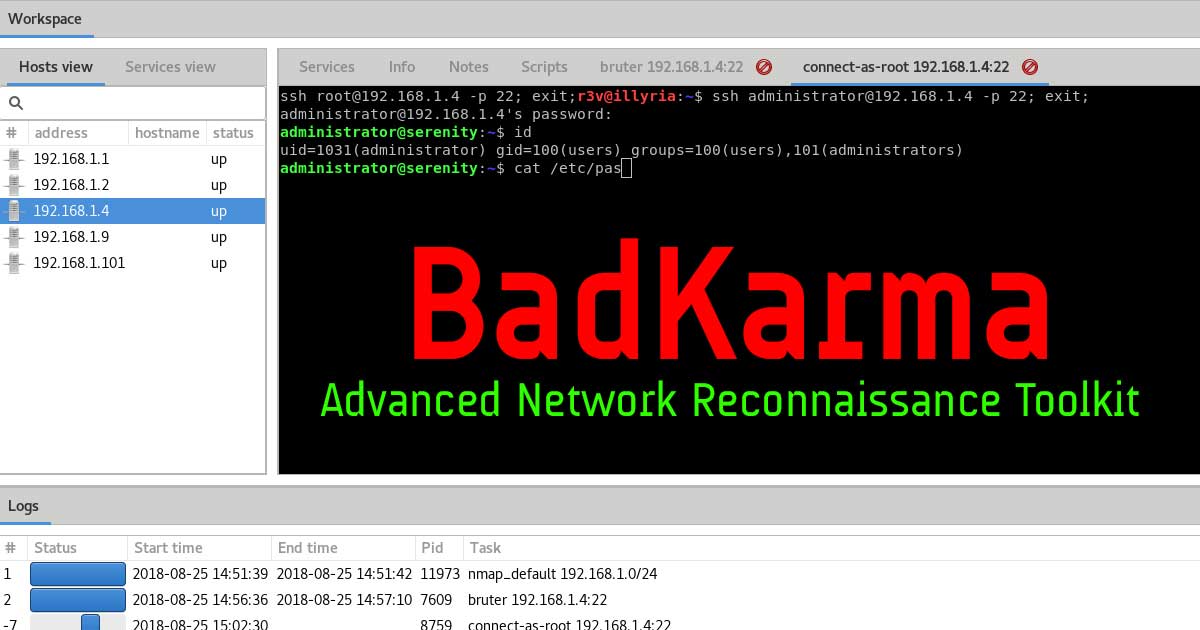
BadKarma is a python3 GTK+ network infrastructure penetration testing toolkit.
Read Details
By providing a target website to the tool, it auto detects its' architecture if using a Content Management Service (CMS).
Read Details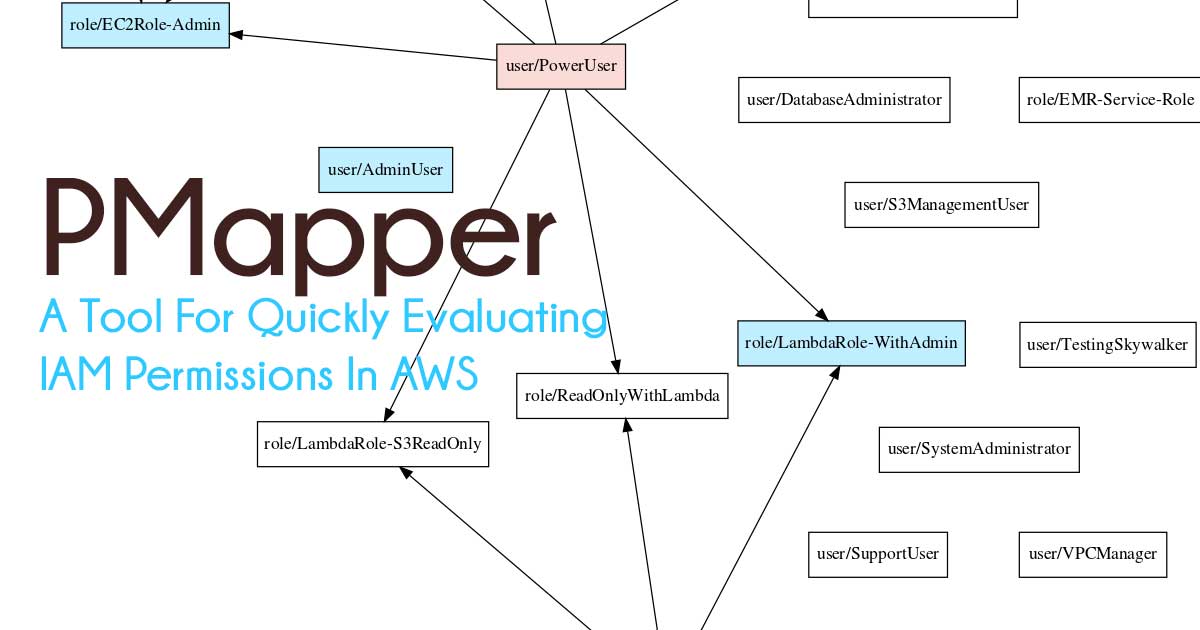
The goal of the AWS IAM auth system is to apply and enforce access controls on actions and resources in AWS. This tool helps identify if the policies in place will accomplish the intents of the account's owners.
Read Details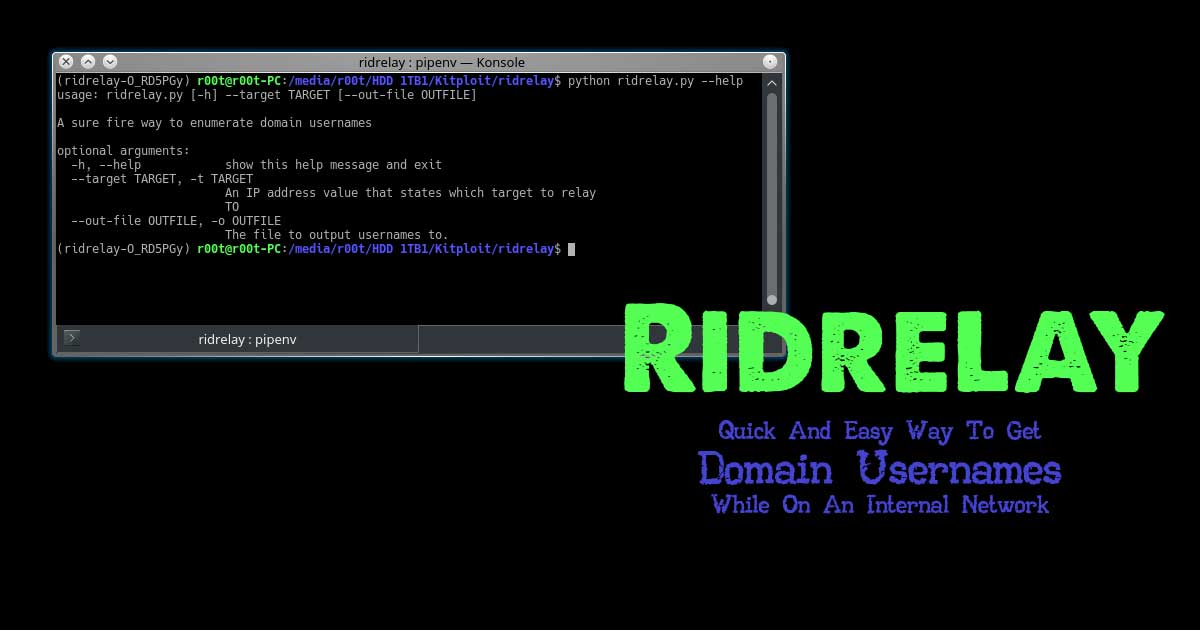
RidRelay combines the SMB Relay attack, common lsarpc based queries and RID cycling to get a list of domain usernames.
Read Details
Tool To Gather Information, based On Operative-Framework
Read Details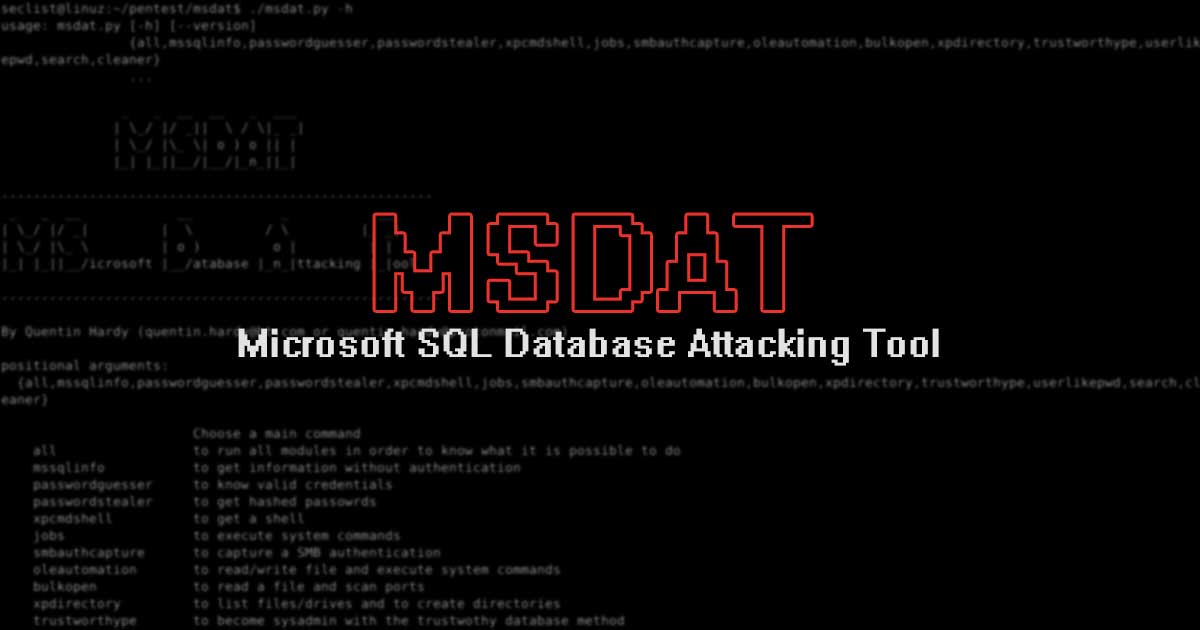
MSDAT (Microsoft SQL Database Attacking Tool) is an open source penetration testing tool that tests the security of Microsoft SQL Databases remotely.
Read Details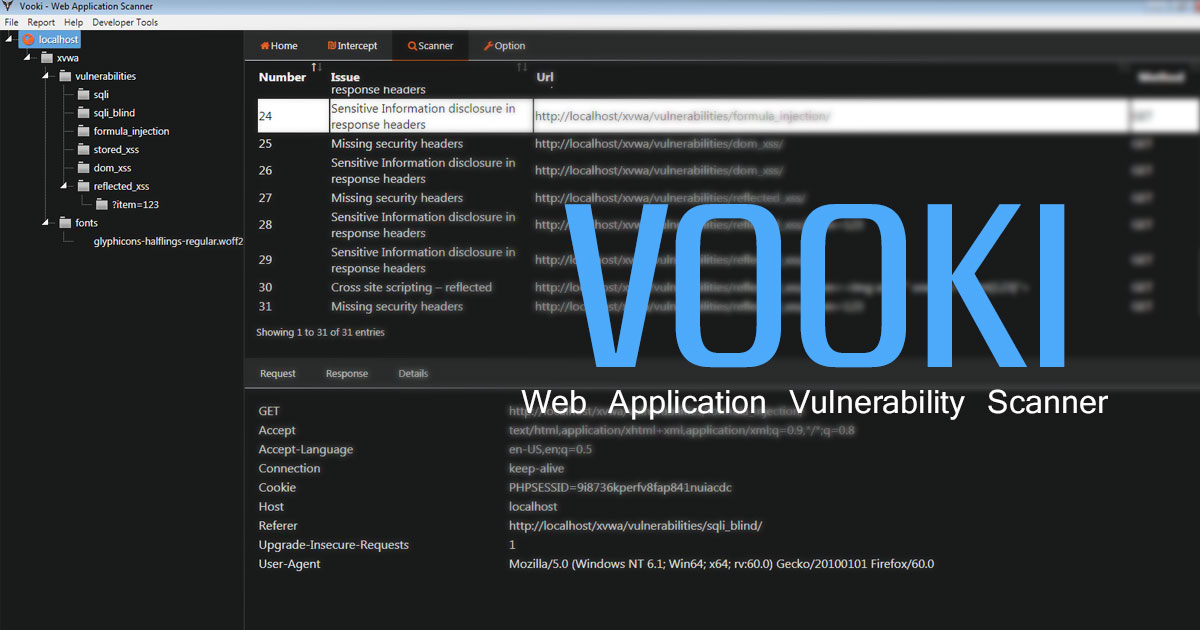
Vooki is a free web application vulnerability scanner. Vooki is a user-friendly tool that you can easily scan any web application and find the vulnerabilities. Vooki includes Web Application Scanner, Rest API Scanner, and reporting section.
Read Details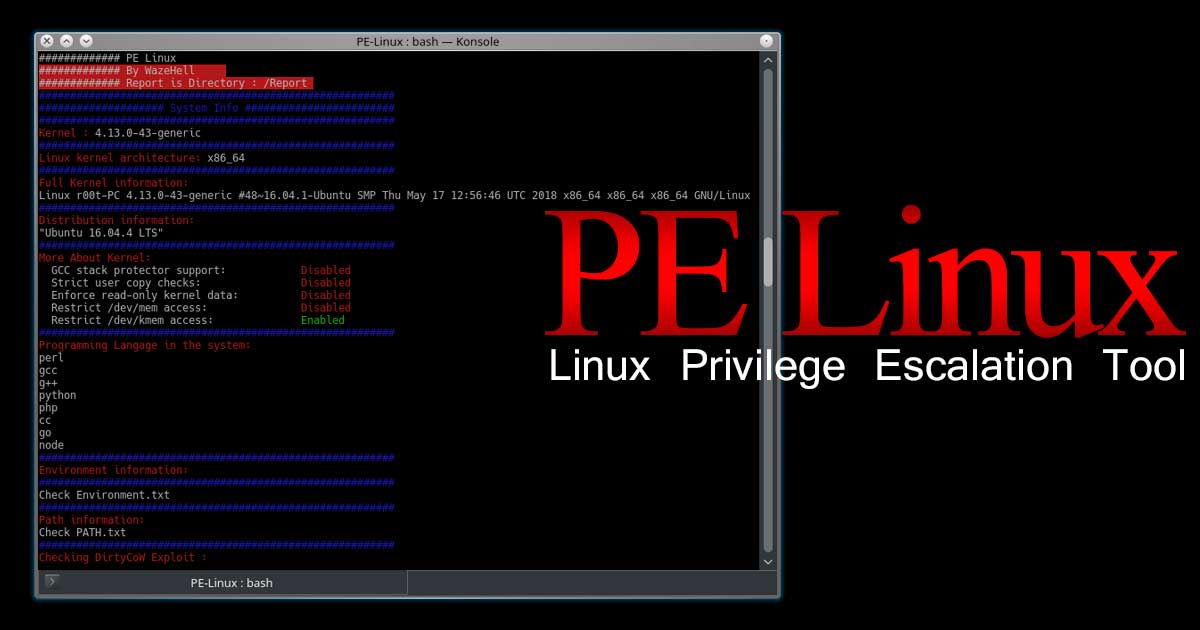
- Getting Started
- System Information Gatherer
- Kernel Information Gatherer
- Checking Development environments on the system (Escaping Restricted Shells)
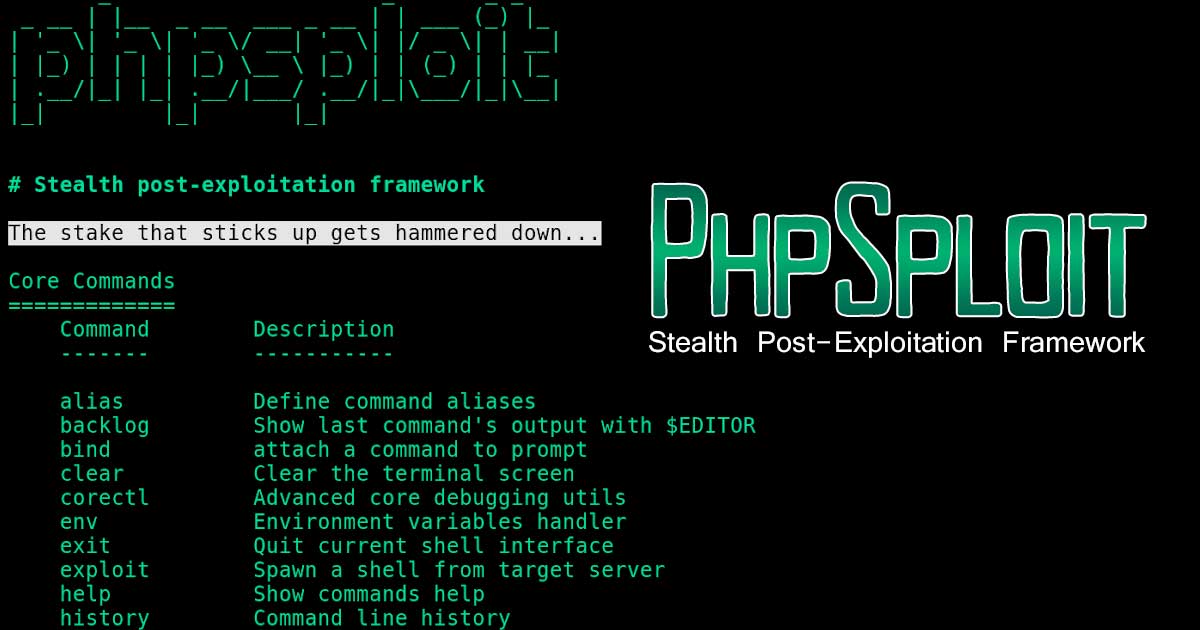
PhpSploit is a remote control framework, aiming to provide a stealth interactive shell-like connection over HTTP between client and web server. It is a post-exploitation tool capable to maintain access to a compromised web server for privilege escalation purposes.
Read Details
In nowadays due to firewall restrictions and patch management policies exploitation of systems has become much more difficult. However one of the most efficient way is the use of client-side attacks.
Read Details
Many routers today use GPON internet, and a way to bypass all authentication on the devices (CVE-2018-10561) was found by VPNMentor.
Read Details
Covert execution is the art of hiding a process. In this case, mimic hides the process in plain sight. mimic can launch any program and make it look like any other program. Any user can use it. It does not require special permissions.
Read Details
Aircrack-ng is a network hacking tool that consists of a packet sniffer, detector, WPA/WPA2-PSK cracker, WEP and an analysis tool for for 802.11 wireless LANs.
Read Details
Make sure that TOR Browser is up and running while working with CLOUDKiLL3R. Make sure that the IP AND PORT are the same in TOR Browser preferences > advanced > Networks
Read Details
A POC tool to demonstrate the risk of unauthorized recording of VoIP and Video, it helps to determine who can eavesdrop, and from what parts of your network.
Read Details
OWASP ZSC is an open source obfuscated code generator tool in Python which lets you generate customized shellcodes and convert scripts to an obfuscated script.
Read Details
Sublist3r is a Python-based tool designed to enumerate subdomains of websites using OSINT. It helps penetration testers and bug hunters collect and gather subdomains for the domain they are targeting.
Read Details
Acunetix is available for Windows XP and higher. Acunetix is a web vulnerability scanner (WVS) that scans and finds out the flaws in a website that could prove fatal.
Read Details
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files.
Read Details
Hacking an Android APK file involves that we decompile, hack it, and recompile, essentially reverse engineering an apk file.
Read Details
Executable compression means compressing an executable file and combining the compressed data with decompression code into a single executable.
Read Details
BitCracker is a mono-GPU password cracking tool for memory units encrypted with the password authentication mode of BitLocker.
Read Details
Bloodhound is a single page Javascript web application, built on Linkurious and compiled with Electron.
Read Details

