Penetration testing, also called pen testing or ethical hacking, is the practice of testing a computer system, network or web application to find security vulnerabilities that a hacker could target. Penetration testing can be automated with software applications or performed manually.
Why learn Network Penetration Testing?
Meeting
Monitoring Necessities
and avoiding penalties
Circumventing the rate of
Network Downtime
Duration
40 hours - 2 classes per week
Eligibility
Completion of Network penetration testing Level I
Course Fees
Class Room Training
Rs.14,750/-
Inclusive of all taxes
Online Training
Rs.24,750/-
Rs.14,750/-
Inclusive of all taxes
What You Will Get?
40 Hours
of in depth training by the best cyber security experts
Study Materials
Network Penetration Testing Level II
Certificate of Completion after examination and alumni status
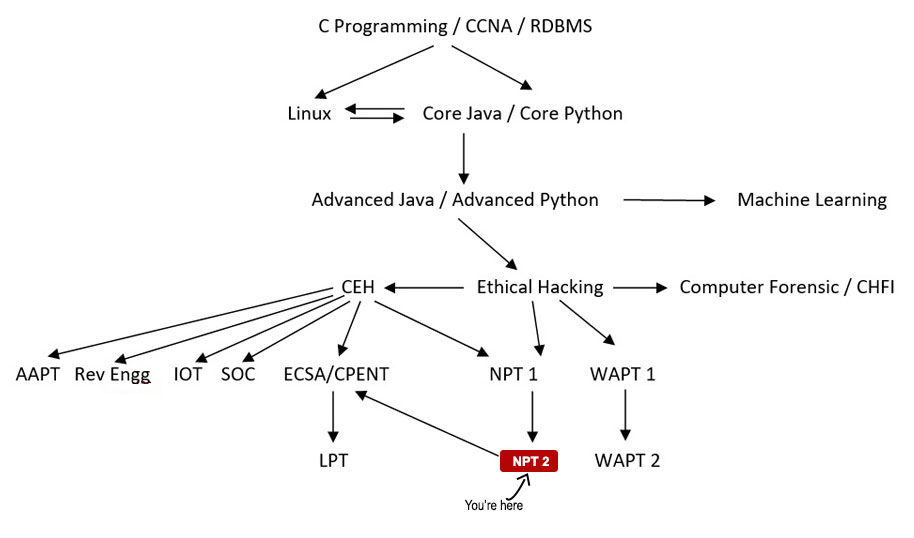
Your Course Path
Course Details
- The duration of the course is 40 hours - 2 classes per week
- The course fee is Rs.14,750/- for classroom and Rs.24,750/- Rs.14,750/- for online
- The course is taught in theory as well as practice
- Introduction to Active Directory (AD) (Day 1)
- AD Architecture and Components (Day 1)
- AD Access control lists and types of authentications used (Day 1)
- Understanding Kerberos Ticketing System (Day 1)
- User and Group Management in AD (Day 1)
- Installing and Configuring Windows Server for AD (Day 3)
- Setting up Domain Controllers (Day 3)
- Creating and Managing Domains and Trusts (Day 3)
- Group Policy Objects (GPOs) in AD (Day 3)
- Introduction to LDAP (Lightweight Directory Access Protocol) (Day 4)
- LDAP Data Interchange Format (LDIF) (Day 4)
- Enumerating AD Using enum4linux, crackmapexec (Day 4)
- Enumerating AD users pre-attack (Day 4)
- Introduction to Responder for Capturing Hashes (Day 5)
- Setting Up and Using Responder in Penetration Tests (Day 5)
- Exploiting NetBIOS and LLMNR to Capture Hashes (Day 5)
- Pass-the-Hash Attacks and Defense Mechanisms (Day 5)
- Exploiting AD Misconfigurations for initial access (Day 5)
- Reconnaissance Techniques for AD (Day 6)
- AD Enumeration (Users, Computers, Domain, Forests, DC, ACL, SPN, Special Permissions) using PowerView and Bloodhound (Day 6)
- Privilege Escalation Techniques in AD Environments (Day 7)
- Data Exfiltration Techniques and Credential Dumping techniques (Day 7)
- Password spray, Overpass the hash attacks (Day 7)
- DCSync, Kerberoasting, ASREPRoasting (Day 7)
- DCSync, Kerberoasting, ASREPRoasting (Day 8)
- Generating and Using Golden Tickets post exploitation (Day 9)
- Creating and Using Silver Tickets post exploitation (Day 9)
- Mitigating Golden/Silver Ticket Attacks (Day 9)
- Using SSH Tunnels for Pivoting (Day 10)
- Proxy Chains and Multi-Hop Tunnelling (Day 10)
- Advanced Local Port Forwarding, Remote Port Forwarding (Day 10)
- Local Privilege Escalation Techniques (Day 11)
- Exploiting Service Permissions and Weaknesses (Day 11)
- Kernel Exploits and DLL Hijacking (Day 11)
- Hunting for Credentials in Memory (Day 11)
- Understanding Buffer Overflows (Day 12)
- Fuzzing Techniques for Vulnerability Discovery (Day 12)
- Crafting Exploits for Buffer Overflows (Day 12)
- Mitigations and Countermeasures (Day 12)
- Setting up a Lab Environment for Buffer Overflow Exploitation (Day 13)
- Exploiting Buffer Overflow in Real-world Applications (Day 13)
- Shellcode Development and Execution (Day 13)
- Exploit Payload Customization (Day 13)
- Setup of Docker Penetration Testing Lab (Day 14)
- Container Enumeration (Day 14)
- Exploiting Docker container for Initial Access (Day 14)
- Linux Capability Exploitation (Day 14)
- Planning and Executing Red Team Engagements (MITRE framework) (Day 15)
- Advanced TTPs (Tactics, Techniques, and Procedures) (Day 15)
- Collaborative Red Team Tools: Empire (Day 15)
- Adversary Simulation and Threat Intelligence Integration (Day 15)
- Practical Challenges in Exploitation and Defences (Day 16)
- Real-world Scenarios and Hands-on Exercises (Day 16)
- Writing Comprehensive Penetration Testing Reports (Day 18)
- CVE and Risk Assessment (Day 18)
- Executive Summary and Technical Details (Day 18)
- Mitigation Recommendations and Roadmap (Day 18)
- Individual or Group Assignment on Advanced Topics in Network Penetration Testing (Day 20)
- Project Presentation (Day 20)
Hacking Tutorials
Read All Tutorials »
Building a career in Digital Forensics - How promising is the future? A thorough career guide
Read Details »Hacking Videos
Explore All Videos »How to Hiding Your Secret File using Steganography?
View On Youtube »Enroll Now
Fields marked with * are mandatory.
Ratings & Reviews
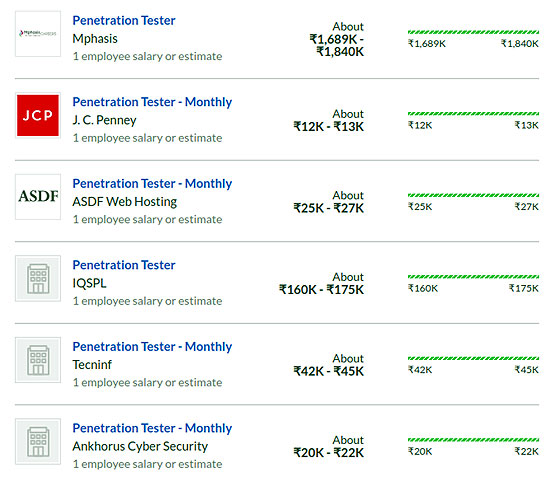
Job Prospects & Job Sources
As per IT industrial study penetration testers have been bracketed with information security analysts. A very high rate of job growth is expected for penetration testing professionals in this field. From 2016 to 2026, as per studies, a 28% rate of growth will be seen in the field of penetrating testing, which is four times the national average job growth rate for all occupations.
The average salary for a Penetration Tester is Rs.6,06,118 per year in India.
A company wise break down of the salary quotient is as follows,
FAQs
Advanced Metasploit (using Scanners, Auxiliary modules, Post-exploitation), Advanced Meterpreter and backdooring, Advanced Malware and PHP Malware, VPN penetration testing, Running non-MSF exploits, Hacking Mail Servers, Reverse TCP Connections, Binding Trojans/Shells to ports, Rooting exploits, SMB exploits, Extracting credentials from system memory, User land to Root exploits for Advanced.
The duration of the course is 40 hours at 2 classes per week.
The course is taught in theory as well as practice.
Completion of Network Penetration Testing Level I for Advanced.
As per IT industrial study penetration testers have been bracketed with information security analysts. A very high rate of job growth is expected for penetration testing professionals in this field. From 2016 to 2026, as per studies, a 28% rate of growth will be seen in the field of penetration testing, which is four times the national average job growth rate for all occupations.
You can go for IOS Penetration Testing, Reverse Engineering & Malware Analysis after this.
Course Fees
Rs.24,750/-Rs.14,750/-
Inclusive of all taxes
Batches
Weekday Batches for Kolkata Center:
Jan, 2026
Jan, 2026
Mar, 2026
Member of: