
- All Courses
- CompTIA Global Courses
-
EC-Council Global Courses
- Certified Ethical Hacker - CEH v13 - AI Powered
- CEH Master
- Certified Penetration Testing Professional - CPENT
- CHFI v10 - Computer Hacking Forensic Investigator
- Certified SOC Analyst (CSA)
- Certified Cybersecurity Technician - CCT
- Certified Cloud Security Engineer - CCSE
- Web Application Hacking and Security - WAHS
- Certified Network Defender - CND v2
- EC-Council - Cyber Security Programs
- Post Graduation Courses
- Graduation Courses
- PG Diploma Courses
- Diploma Courses
- Vocational Training Courses
-
Skill Development Short Term Courses
- Ethical Hacking
- Computer Forensic
- SOC Analyst Fundamental
- Core Python Programming
- Advanced Python Programming
- CCNA Essentials & Ethical Hacking Combo
- Web Application Penetration Testing Level I
- Web Application Penetration Testing Level II
- Network Penetration Testing Level I
- Network Penetration Testing Level II
- Reverse Engineering & Malware Analysis
- Bug Bounty Hunting
- CCNA Essential
- Firewall Administration
- A-Z Defense in Comp Security - For Corporates
IDS - Intrusion Detection Systems
Require Further Information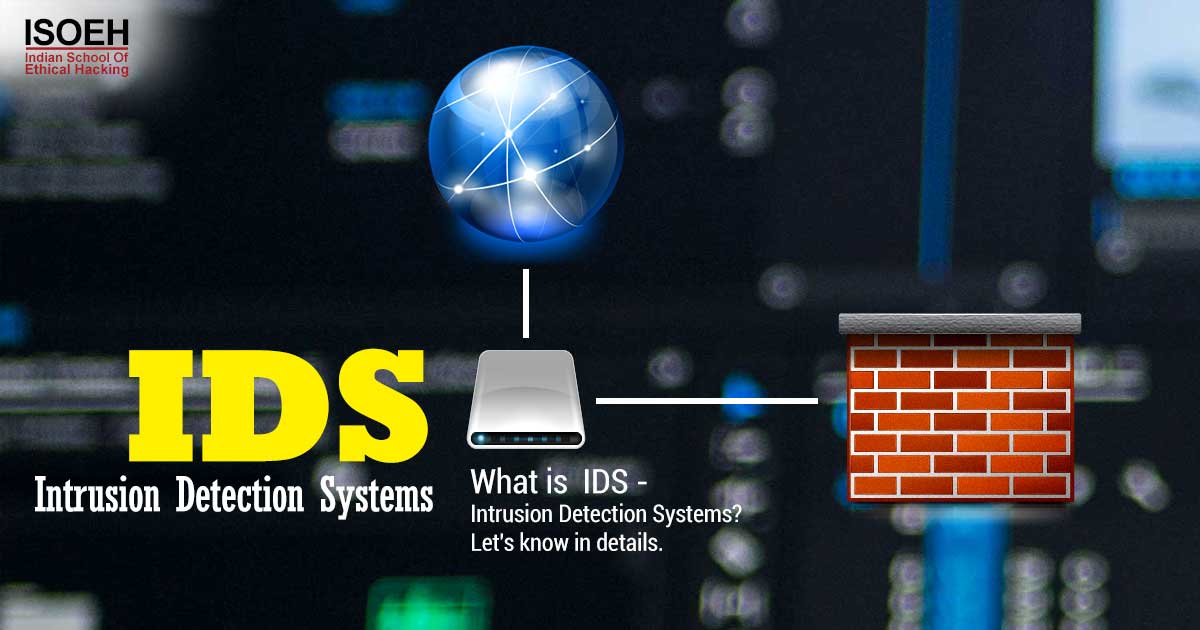
Let's learn today on IDS - Intrusion Detection Systems: isoeh
NIDS vs HIDS
- Host-based IDS
An agent on a host identifying intrusions by analyzing system calls, application logs, file-system modifications (binaries, password files, capability databases, Access control lists, etc.) and other host activities and state.
In a HIDS, sensors usually consist of a software agent. Some application-based IDS are also part of this category. An example of a HIDS is OSSEC.
- Network NIDS
Platform identifying intrusions by examining network traffic and monitors multiple hosts.
- Gain access to network traffic by connecting to a network devices for port mirroring, or a network tap.
Placement:
- Sensors are placed at choke points in the network to monitor,in the demilitarized zone (DMZ) or at network borders.
PIDS vs VMDS
- Perimeter IDS
- Detects & pinpoints location of intrusion attempts on perimeter fences of critical infrastructures
- Electronics or advanced fiber optic cable technology in perimeter fence,for detection of disturbances on the fence
- VM based IDS
Detect intrusions using virtual machine monitoring.
Read Other Tutorials
Read All Tutorials »
Flutter in Mobile App development - Pros & Cons
Read Details »
3 Signs Your Twitter Account Has Been Hacked & How To Recover It
Read Details »
How to check a suspicious link without clicking on it?
Read Details »
ATM Skimming: The latest high-tech ATM Fraud in Kolkata
Read Details »
Social Engineering – learn about Techniques & Prevention
Read Details »
What is crypto-jacking? How to protect yourself from it?
Read Details »
Artificial Intelligence & Machine Learning – What's the difference between them?
Read Details »
Want to shine as a Penetration Tester? Check out what skills do you require
Read Details »
Machine Learning, the booming career option shaping the job market
Read Details »
Tips to Become an Ethical Hacker with CEH v9 Bootcamp!
Read Details »
Is your child a victim of cyber-bullying? Stop it now!
Read Details »
5 terrifying ways your phone can get hacked
Read Details »
Want to become a successful bug bounty hunter? Follow the steps!
Read Details »
Top 5 Wifi hacking tools
Read Details »
Quick tip: For all those annoyed with utorrent ads
Read Details »
IDS - Intrusion Detection Systems" title="IDS - Intrusion Detection Systems
Read Details »
Payment Card IndustryData Security Standard in nutshell
Read Details »
What goes into selecting a Web Pentesting consultant?
Read Details »Hacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details
