All actions that take place within the SOC are largely under the control of a Security Operation Centre Analyst. Security operations analysts collaborate with security engineers and SOC managers to identify, contain, and eliminate IT threats in order to provide situational awareness. Cybercriminals are adopting a variety of breaching techniques to harm the computer system due to the increase in cyber threats and intrusions. They need an Analyst who is in charge of managing its security activities as a result. SOC is for Security operation Centre, and it refers to the division and group of cyber security experts who keep an eye on the company's network and data for cyberattacks and other occurrences in real time.
An in-depth programme called SOC Analyst Fundamental (Pro/Advance) is the prerequisite for working at a security operations centre (SOC). It is designed to help present and future Tier I and Tier II SOC analysts become proficient in carrying out operations at the entry-level and intermediate level. Such a training and certification programme aids the candidate in gaining cutting-edge technical abilities that are in high demand by providing instruction from some of the most knowledgeable teachers in the field. Through thorough, meticulous knowledge and advanced level capabilities for dynamically contributing to a SOC team, the programme focuses on opening up new job prospects. Before imparting the knowledge of log management and correlation, SIEM implementation, advanced incident detection, and incident response, it discusses the foundations of SOC operations in great detail.
Why to Choose this Course?
A SOC team offers
high-quality IT security services
to detect potential cyber threats/attacks actively and quickly respond to security incidents.
To handle sophisticated threats,
enterprises need ADVANCED cyber security solutions
along with traditional methods of defense.
A SOC Analyst continuously
monitors and detects potential threats,
triages the alerts, and appropriately escalates them.
Organizations need
skilled SOC Analysts who can serve as the FRONT-LINE defenders,
warning other professionals of emerging and present cyber threats.
Duration
24 hours - 2 classes per week
Eligibility
Graduate and one year of work experience in the Network Admin/Security.
Course Fees
Class Room Training
Rs.19,000/-
Inclusive of all taxes
Online Training
Rs.29,000/-Rs.19,000/-
Inclusive of all taxes
What You Will Get?
24 Hours
in-depth training by best faculties from cyber security industry
Study Materials
and examination voucher
SOC Analyst Fundamental Certificate
of completion after examination and alumni status
Course Benefits:
Learning Objectives of SA
- Gain Knowledge of SOC processes, procedures, technologies, and workflows.
- Gain basic understanding and in-depth knowledge of security threats, attacks, vulnerabilities, attacker’s behaviours, cyber kill chain, etc.
- Able to recognize attacker tools, tactics, and procedures to identify indicators of compromise (IOCs) that can be utilized during active and future investigations.
- Able to monitor and analyze logs and alerts from a variety of different technologies across multiple platforms (IDS/IPS, end-point protection, servers and workstations).
- Gain knowledge of Centralized Log Management (CLM) process.
- Able to perform Security events and log collection, monitoring, and analysis.
- Gain experience and extensive knowledge of Security Information and Event Management.
- Gain knowledge on administering SIEM solutions (Splunk/AlienVault/OSSIM/ELK).
- Understand the architecture, implementation and fine tuning of SIEM solutions (Splunk/AlienVault/OSSIM/ELK).
- Gain hands-on experience on SIEM use case development process.
- Able to develop threat cases (correlation rules), create reports, etc.
- Learn use cases that are widely used across the SIEM deployment.
- Plan, organize, and perform threat monitoring and analysis in the enterprise.
- Able to monitor emerging threat patterns and perform security threat analysis.
- Gain hands-on experience in alert triaging process.
- Able to escalate incidents to appropriate teams for additional assistance.
- Able to use a Service Desk ticketing system.
- Able to prepare briefings and reports of analysis methodology and results.
- Gain knowledge of integrating threat intelligence into SIEM for enhanced incident detection and response.
- Able to make use of varied, disparate, constantly changing threat information.
- Gain knowledge of Incident Response Process.
- Gain understating of SOC and IRT collaboration for better incident response.
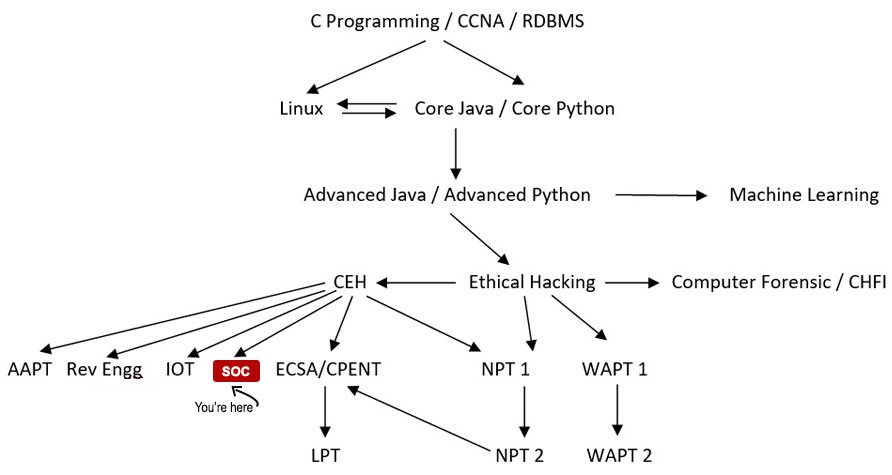
Your Course Path
Course Details
- The lab-intensive SOC Analyst Fundamental training program emphasizes the holistic approach to deliver elementary as well as advanced knowledge of how to identify and validate intrusion attempts.
- Through this, the candidate will learn to use SIEM solutions and predictive capabilities using threat intelligence.
- The program also introduces the practical aspect of SIEM using advanced and the most frequently used tools.
- The candidate will learn to perform enhanced threat detection using the predictive capabilities of Threat Intelligence.
- Overview of SOC functions and responsibilities (Day 1)
- Understanding the SOC analyst role (Day 1)
- Introduction to the incident response lifecycle (Day 1)
- Overview of common cyber threats and attack vectors (Day 2)
- Understanding threat actors and their motivations (Day 2)
- Current trends in cyber attacks (Day 2)
- Introduction to security event monitoring and log analysis (Day 3 & 4)
- Common security event sources (logs, network traffic, system alerts) (Day 3 & 4)
- Log analysis techniques and tools (Day 3 & 4)
- Techniques for detecting security incidents (Day 5)
- Incident classification and severity levels (Day 5)
- Establishing incident response priorities (Day 5)
- Incident response planning and frameworks (e.g., NIST, ISO 27035) (Day 6)
- Incident response roles and responsibilities (Day 6)
- Incident containment and eradication strategies (Day 6)
- Introduction to threat intelligence (Day 7)
- Threat hunting methodologies and tools (Day 7)
- Leveraging threat intelligence in SOC operations (Day 7)
- Overview of vulnerability management processes (Day 8)
- Prioritizing and remediating vulnerabilities (Day 8)
- Patch management best practices (Day 8)
- Techniques for investigating security incidents (Day 9)
- Digital forensics fundamentals (Day 9)
- Preserving and analyzing digital evidence (Day 9)
- Creating incident reports and documenting findings (Day 10)
- Communication strategies for different stakeholders (Day 10)
- Presenting incident analysis and recommendations (Day 10)
Hacking Tutorials
Read All Tutorials »
Building a career in Digital Forensic - How promising is the future? A thorough career guide
Read Details »Hacking Videos
Explore All Videos »How to Hiding Your Secret File using Steganography?
View On Youtube »Enroll Now
Fields marked with * are mandatory.
Ratings & Reviews
Job Prospects & Job Sources
The Profiles that count for SOC Analyst Fundamental Individuals include the following:
| SOC Analyst | Information Security Analyst | IT Security Analyst | Cyber Threat Analyst |
The average salary of SOC analyst in India is Rs 4 lakhs per annually.
FAQs
- Introduction to Security Operations Center (SOC)
- Cyber Threat Landscape
- Security Event Monitoring and Analysis
- Security Incident Detection and Classification
- Security Incident Response Procedures
- Threat Intelligence and Threat Hunting
- Vulnerability Management and Patching
- Security Incident Investigation
- Security Incident Reporting and Communication
24 hours
- SOC Analyst Fundamental (Tier I and Tier II)
- Network and Security Administrators, Network and Security Engineers, Network Defense Analyst, Network Defense Technicians, Network Security Specialist, Network Security Operator, and any security professional handling network security operations
- Cybersecurity Analyst
- Entry-level cybersecurity professionals
- Anyone who wants to become a SOC Analyst
Complete 12th board exam and basic networking knowledge or CCNA.
This Pro/Advance program focuses on creating new career opportunities through extensive, meticulous knowledge with enhanced level capabilities for dynamically contributing to a SOC team.
You can upgrade your career by doing a Global Certification Course (CSA- Certified SOC Analyst) from EC-Council and then apply to join a security operations center (SOC).
Course Fees
Rs.29,000/-Rs.19,000/-
Inclusive of all taxes
Batches
Weekend Batches for Bhubaneswar Center:
Apr, 2025
Apr, 2025
Jun, 2025
Member of: