Apple acknowledges ISOEH for reporting its website encryption vulnerability

The Apple website was not secure. While surfing the Apple site http://www.apple.com/, we have found several encryption related vulnerabilities.
Here are those:
1) www.apple.com site was supporting SSL 2.0(on port 443) cipher with weak encryption as follows:
DES -CBC-MD5- 56 bits.
EXP-RC2-CBC-MD5 40 bits.
EXP-RC4-MD5- 40 bits.
Recommendation:
The support of SSL 2.0 should be removed as it is outdated weak encryption. Any encryption below 128 bit is weak.
2) In SSL v3.0 the site was supporting few weak encryption as follows which a malicious user can exploit:
EXP-DES-CBC-SHA 40 bits.
EXP-RC2-CBC-MD5 40 bits
EXP-RC4-MD5 40 bits.
Recommendation:
The support of all these weak encryption should be removed. Any encryption below 128 bit is weak.
3) The site was supporting TLS v1 which is strong but the following encryption in TLS should be removed.
EXP-DES-CBC-SHA 40 bits.
4) The webserver /lib/prototype.js file was affected.
This page did not exist. By requesting a page that did not exist more fully qualified path names were found. From this information an attacker might learn the file system structure from the web server. This information could be used to conduct further attacks.
Recommendation:
The information should not be available to the user. Apple needed to configure their server or web application not to return this information.
5) A possible sensitive directory had been found at following directories
/CVS, /data, /downloads, /downloads/scripts, /global, /hotnews/scripts, /reseller.
It looks for common sensitive resources like back up directories, database dumps, administration pages.
Each one of these directories could help an attacker to learn more about the target. This directory may expose sensitive information that could make a malicious user to prepare for further attack.
Recommendation:
Restricting access to these directories or removing it.
We had mailed it to Apple team along with countermeasures.
Apple development center has sent us an appraisal letter. Here is the part of the letter:
Appraisal letter from Apple:-
Follow-up: 162664922
Re: Apple Developer Feedback
Hello Abir,
Thank you for contacting Apple Developer Support regarding the Developer website.
We appreciate that you have taken the time to send us your feedback. Please be assured that all of your comments have been forwarded to the appropriate Apple team.
If you have further questions or comments, please let us know.
Best regards,
Madoka Nakamura
Apple Developer Support
Forbes website flaw revealed by ISOEH

Forbes is a popular American business magazine which features original articles on finance, industry, investing, and marketing topics. It also reports on related subjects such as technology, communications, science, politics, and law. It is one of the most top listed international business magazine which provides "Information for the World's Business Leaders" as claimed by them.
The truth is, even their site got vulnerabilities which are considered as severe in hacking world.
Well, our Hackingheart team revealed the truth. Hackingheart team had conducted a security testing on www.forbes.com, Forbes's official web site and they were simply shocked when they found the following vulnerabilities:
- Shocking enough that, Forbes site was vulnerable to XSS attack, which was listed under the top 10 web vulnerabilities by OWASP in 2010.
- Forbes were using older version of Apache web site which itself vulnerable to several malicious web attacks.
- Attacker could execute code to escalate privilege.
- There were several pages that could be hijacked using Man-In-The-Middle attack.
Hackingheart team conducted this testing simply for their curiosity and thirst of knowledge but when we discovered the above mentioned vulnerabilities (we have listed only those vulnerabilities considered as crucial) we were astonished. "World's top listed magazine's website is itself vulnerable to malicious attacks? – This had become one of the biggest questions for us. The fact also revealed that they were not aware of the necessity of web application penetration testing, because if they would, we would not have been posting this article.
A small piece of advice from us is, if you are afraid of hacking, then at least try to know how to protect yourself a little bit. Because, you never know, the next target might be you!
ISRO site vulnerability exposed by ISOEH

Indian Space Research Organization (http://www.isro.org) was vulnerable to session hijack. This vulnerability was exposed by ISOEH team member, Abir Atarthy.
We had mailed ISRO regarding this. The details were as follows:
Vulnerability description:
Cookie Not Marked As HttpOnly:-
HTTPOnly cookies cannot be read by client-side scripts therefore marking a cookie as HTTPOnly can provide an additional layer of protection against Cross-site Scripting attacks.
Identified Cookie:
ASP.NET_SessionId
Vulnerability Classifications:
OWASP A6 CWE-16
Impact:
During a Cross-site Scripting attack an attacker might easily access cookies and hijack the victim's session.
Remedy:
Consider marking all of the cookies used by the application as HTTPOnly. After these changes javascript code will not able to read cookies.
Sikkim Manipal University login breach discovered & reported to SMU

Sikkim Manipal University portal was vulnerable to SQL Injection attack.
Details:
About the university:
Sikkim Manipal is one of the largest private Universities in India. The Institute attracts students from all over the country, with over 1700 students enrolled in the various engineering disciplines. 102 full-time faculties are employed. ISOEH revealed a login breach in the SMU site.
Type of problem:
SQL Injection
Vulnerable Portal:
http://portal.smude.edu.in/
User Name: *sanjay*
[any name will work]
Password: *' OR ''='
*Choose "*Center Login*" radio button
Press SUBMIT.
Screenshot:
Effect:
Once you had the access to the main admin panel there were options to download & print ALL student records, contact information, admit cards for upcoming examinations, assignments, results, etc. One could also change the password then.
Credit:
Pradip Sharma, Surajit Biswas, Sandeep Sengupta;
Cyber Security Research Analysts, iSolution Software Systems Pvt. Ltd. (ISOEH was an associated company of iSolution Software Systems Pvt. Ltd.)
www.isolutionindia.com
Calcutta University website was spreading malware via iframe code insertion

Calcutta University is the oldest existing University in Indian Subcontinent. Founded 1857, it is ranked 39th in the world.
Vulnerability:
The main page of their site was spreading virus. www.caluniv.ac.in.
It had iframe code injection & was pulling virus from the Russian site pantscow.ru. Thousand could be infected while checking results on the website.
Screenshot:
Credit:
Arnab Kanti Choudhury, Sandeep Sengupta;
Cyber Security Research Analysts
iSolution Software Systems Pvt. Ltd. (ISOEH was an associated company of iSolution Software Systems Pvt. Ltd.)
www.isolutionindia.com
Disclaimer:
The above information has been published with intention that the concerned authorities will take notice & amend the bugs. People are requested not to use the above information for illegal actions. We take no responsibility of the consequences.
IGNOU website – SQL Injection, Weak Authentication reported

IGNOU currently serves millions of students in India and 40 countries abroad in twenty one schools and a network of 59 regional centers, 7 sub-regional centers, 2600 study centers, and 52 overseas centers.
IGNOU website is somehow vulnerable to SQL Injection & Weak Authentication Vulnerability. Some modules of site www.ignou.ac.in have weak authentication, SQL Injection problems.
These modules seem to have weak authentication:
- http://www.ignou.ac.in/placement_portal/login
- http://www.ignou.ac.in/ignou/studentzone/queries/3
- http://aciil.ignou.ac.in/Survey/
- http://aciil.ignou.ac.in/Survey/Login.jsp
A huge student database was accessible having all the personal information like Name, Reg.No., Email Ids, Course enrolled, Address, Moble No. etc. Over a Million records was at stake.
Faculty Use:
- http://webserver.ignou.ac.in/bsfeedback/totalemail.asp
- http://webserver.ignou.ac.in/newsite.html
Informed the concerned authorities, admin about the issues to patch up the vulnerabilities.
BSNL - Dotsoft (Admin) Auth Bypass Vulnerability

The database of Calcuttatelephones.com was containing 2600 plus records.
Click the above link to see the full disclosure.
Vulnerability on Flipkart reported by ISOEH Team Member

Our team member Kirit Sankar Gupta had reported vulnerability on Flipkart. As a token of appreciation, Flipkart has now added his name on HALL OF FAME for Security Disclosure.
Here is the screenshot: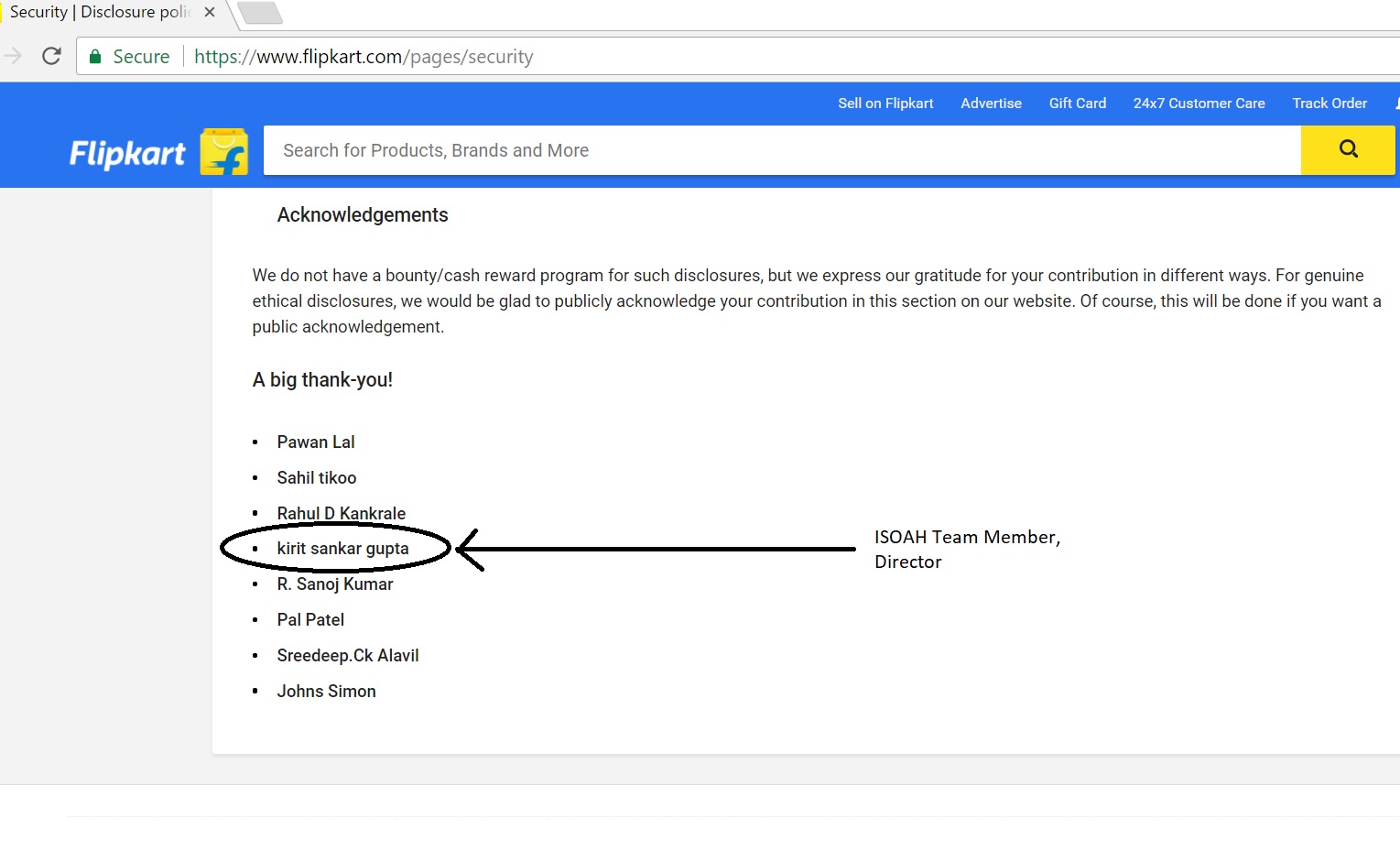
Exclusive Blog
Read All Exclusive Blog »
According to Check Point, during the period July to December 2017, one in five Organizations are affected by crypto mining malware, tools that enable cybercriminals to hijack the victim's CPU or GPU power and existing resources to mine cryptocurrency, using as much as 65% of the end-users CPU power.
Read DetailsHacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read Details

