
Contents
Introduction
 Access to the Internet was limited via devices like the desktop, tablet or smartphone. Still, as we move towards the future, our cities are becoming smarter, integrating the Internet of Things (IoT) to enhance urban life. However, this technological evolution brings significant security challenges. In this blog, we’ll explore the key security hurdles smart cities face and discuss robust strategies to mitigate these risks, ensuring a safer, smarter urban environment.
Access to the Internet was limited via devices like the desktop, tablet or smartphone. Still, as we move towards the future, our cities are becoming smarter, integrating the Internet of Things (IoT) to enhance urban life. However, this technological evolution brings significant security challenges. In this blog, we’ll explore the key security hurdles smart cities face and discuss robust strategies to mitigate these risks, ensuring a safer, smarter urban environment.
Before starting about IoT security challenges, let’s talk about what is IoT. We are taking all the things in the world and connecting them to the internet. When those are connected to the internet, they can send information, receive information or do both. These makes things smart. IoT has 4 main components – 1) Sensors, 2) Connectivity, 3) Data Processing & 4) User Interface. IoT devices have apps so that users can control them remotely. IoT is revolutionizing what’s possible across civic sectors.
The Rise of Smart Cities: A Double-Edged Sword
 Smart cities use IoT technology to streamline various urban operations, including traffic management, waste disposal, and energy use, making life more convenient for residents and helping urban planners manage cities more effectively. Despite these benefits, the integration of IoT devices into city infrastructures introduces complex security vulnerabilities that need addressing. Manufacturers should implement robust security measures such as strong authentication, encryption, regular firmware updates, and secure coding practices to protect IoT devices from unauthorized access and tampering.
Smart cities use IoT technology to streamline various urban operations, including traffic management, waste disposal, and energy use, making life more convenient for residents and helping urban planners manage cities more effectively. Despite these benefits, the integration of IoT devices into city infrastructures introduces complex security vulnerabilities that need addressing. Manufacturers should implement robust security measures such as strong authentication, encryption, regular firmware updates, and secure coding practices to protect IoT devices from unauthorized access and tampering.
As the world increasingly demands the Internet of Things, we face many challenges. Let's learn about the most significant challenges or risks associated with IoT and how it affects our everyday lives. We will also see how to protect ourselves because most IoT devices are vulnerable because they lack the necessary built-in security controls to defend against threats.
1. Vast Attack Surface
 The sheer number of connected devices in a smart city creates a vast attack surface. Each device, from traffic sensors to public Wi-Fi systems, potentially serves as an entry point for cyberattacks. An attack surface is how you appear to the outside world. It is a representation of the perimeter of a company that an attacker can go after. And the reason why knowing your attack surface is extremely important is because the first stage in any hack is reconnaissance. Hacker goes and tries to discover as much as possible about the target.
The sheer number of connected devices in a smart city creates a vast attack surface. Each device, from traffic sensors to public Wi-Fi systems, potentially serves as an entry point for cyberattacks. An attack surface is how you appear to the outside world. It is a representation of the perimeter of a company that an attacker can go after. And the reason why knowing your attack surface is extremely important is because the first stage in any hack is reconnaissance. Hacker goes and tries to discover as much as possible about the target.
2. Data Privacy Concerns
IoT devices collect massive amounts of data to function effectively including personal and sensitive information. This data often includes sensitive personal information, making it a prime target for breaches, with implications for citizen privacy and trust. Top IoT security problems are Denial of Service attacks (DoS), Distributed Denial of Service attacks (DDoS), Unauthorized Access, Information Manipulation, and Information Disclosure.
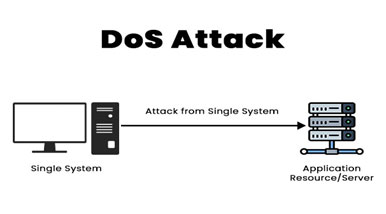 What is DoS? It means the server is not giving services to the user. Here user may be an authorized user but still server is still denying the services. How this is happening? Maybe hackers or attackers are sending so many requests to the server. So as if the server is receiving so many requests. Then the server will think that the network is too busy. If the network is too busy, the server may deny the services. So, here in this way a hacker is flooding the request over here to the system. In this case, an attacker may use the device itself, or the centralized network. Then they are flooding the endpoint devices with so much traffic that they cannot complete the work they were intended to do.
What is DoS? It means the server is not giving services to the user. Here user may be an authorized user but still server is still denying the services. How this is happening? Maybe hackers or attackers are sending so many requests to the server. So as if the server is receiving so many requests. Then the server will think that the network is too busy. If the network is too busy, the server may deny the services. So, here in this way a hacker is flooding the request over here to the system. In this case, an attacker may use the device itself, or the centralized network. Then they are flooding the endpoint devices with so much traffic that they cannot complete the work they were intended to do.
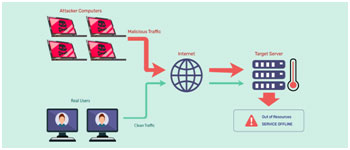 What is DDoS? It means that so many devices not get services from the server. How this is happening? Here, hackers send corrupted data or viruses to the devices. So, because of the virus getting installed inside the devices, what happens is when these devices are forwarding requests at that time, the server is denying the service. The reason is a server thinks that this request is not coming as per authorized access. So, multiple users get a Denial of Service from the server/ system.
What is DDoS? It means that so many devices not get services from the server. How this is happening? Here, hackers send corrupted data or viruses to the devices. So, because of the virus getting installed inside the devices, what happens is when these devices are forwarding requests at that time, the server is denying the service. The reason is a server thinks that this request is not coming as per authorized access. So, multiple users get a Denial of Service from the server/ system.
 What is Unauthorized Access? It means an authorized user is not accessing the system. In this case, the hacker hacks the access of the authorised user and even can give commands to the server too. So, the server thinks that this user is forwarding a command. But practically those commands are forwarded by the hacker. Through this, attackers can steal data, simply they can do anything with the system.
What is Unauthorized Access? It means an authorized user is not accessing the system. In this case, the hacker hacks the access of the authorised user and even can give commands to the server too. So, the server thinks that this user is forwarding a command. But practically those commands are forwarded by the hacker. Through this, attackers can steal data, simply they can do anything with the system.
What is Information Manipulation? It means that it can be done as if there is access to the information. How it happens? It happens on a device side, a server side or on the database side. Hacker takes access to the unauthorized user or takes access to the system.
What is Information Disclosure? Nowadays lots of spam calls, messages, and false audio or video are coming due to information leakage. Hackers can take information from many resources.
Privacy should be a priority, and data protection regulations, such as the General Data Protection Regulation (GDPR) should be followed. This includes obtaining user consent for data collection, anonymizing or pseudonymizing data when possible, and implementing privacy-by-design principles.
3. Interconnectivity Risks
The interconnected nature of IoT devices means that a breach in one device can lead to a domino effect, compromising multiple aspects of city operations. This interconnectivity magnifies the impact of any single security incident.
4. Lack of Standardization
Currently, there is a significant variation in the security measures adopted by different IoT devices, primarily due to the lack of standardized security protocols across platforms. This inconsistency can lead to vulnerabilities.
5. Resource Constraints
Many IoT devices operate with limited processing power and storage, which restricts their ability to implement sophisticated security measures.
Also, there are a lot of other issues like device similarity, problematic deployment, no upgrade support, insecure communications etc.
Strategies to Fortify IoT in Smart Cities

1. Implementing Robust Security Frameworks
Cities must adopt comprehensive security frameworks that include encryption, secure boot, and multi-factor authentication to safeguard data integrity and privacy. Regular security audits and updates can further reinforce defences.
2. Promoting Standardization and Compliance
Encouraging the development and adoption of industry-wide security standards can minimize vulnerabilities. Compliance with frameworks like the National Institute of Standards and Technology (NIST) guidelines for IoT security is crucial.
3. Enhancing Data Privacy Measures
 What is Data Privacy? It is concerned with the proper handling, storage and usage of personal information. It is all about the rights of individuals concerning their personal information. The most common concerns regarding data privacy are – 1) Managing contracts or policies, 2) Applying governing regulation or law (like GDPR), & 3) Third-party management. Smart cities should prioritize data privacy by implementing strict data access controls and ensuring that data collection complies with privacy laws and regulations. Techniques such as data anonymization can protect individual privacy without compromising the functionality of IoT systems.
What is Data Privacy? It is concerned with the proper handling, storage and usage of personal information. It is all about the rights of individuals concerning their personal information. The most common concerns regarding data privacy are – 1) Managing contracts or policies, 2) Applying governing regulation or law (like GDPR), & 3) Third-party management. Smart cities should prioritize data privacy by implementing strict data access controls and ensuring that data collection complies with privacy laws and regulations. Techniques such as data anonymization can protect individual privacy without compromising the functionality of IoT systems.
4. Leveraging Artificial Intelligence
AI and machine learning can be powerful tools in identifying and responding to potential threats in real-time. These technologies can help predict and mitigate attacks before they cause harm.
5. Fostering Public-Private Partnerships
Collaborations between city governments, technology providers, and cybersecurity experts can lead to the sharing of knowledge, resources, and best practices, enhancing the security posture of smart cities.
Conclusion
We are continuing to embrace the convenience and efficiency of smart cities; we must also intensify our efforts to address the inherent security challenges. By implementing robust security measures, standardizing protocols, and leveraging advanced technologies, we can protect these urban environments from potential threats. Ensuring the security of IoT devices in smart cities is not just about safeguarding technology but about preserving the trust and safety of all citizens. Let's commit to building resilient smart cities where technology serves us safely and effectively.
Hacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details
















