
Contents
- Introduction to Cybersecurity and Information Security: What Are They and How Are They Different?
- Cybersecurity vs. Information Security: Definitions
- Types of Cybersecurity Threats and How to Mitigate Them
- Types of Digital Security Risks
- The Benefits of Investing in Cybersecurity Training
- What Is Involved in an Ethical Hacking Course?
- Benefits Of Becoming a Certified Cybersecurity Technician
- Conclusion
Introduction to Cybersecurity and Information Security: What Are They and How Are They Different?
Professionals must become more knowledgeable about the distinctions between information security and cybersecurity as the cybersecurity institution develops traction to mitigate data security threats. It is imperative to be able to differentiate between an ethical hacking school and a certified cybersecurity technician programme. We'll help you distinguish between information security and cybersecurity in this in-depth tutorial so you can evaluate your personal needs and choose a career path that suits you.
Cybersecurity vs. Information Security: Definitions
It's crucial to comprehend the fundamental differences between information security and cybersecurity before delving into their specifics. To put it simply, cybersecurity is the discipline of defending data, systems, programmes, and networks against harmful intrusions. A variety of technologies, including firewalls, antivirus programs, encryption, and more, are used to do this. Information security, on the other hand, is concerned with safeguarding data by limiting access or stopping illegal access.
To preserve the privacy, availability, and integrity of data, information security entails keeping an eye out for and reacting to IT threats. To do this, rules and guidelines governing user interaction with computers and networks must be put in place. Furthermore, physical security measures like locked cabinets and limited places are part of information security.
Types of Cybersecurity Threats and How to Mitigate Them
Businesses and organisations all around the world are becoming increasingly concerned about cybersecurity. Data security risks grow in tandem with technological advancements. Offering ethical hacking training and credentials such as the Certified Cybersecurity Technician, the Cyber Security Institute (CSI) gives important information about safeguarding data against online attacks.
 Risks to data security can take many different forms, including malicious software, online theft of private data, and even outsiders gaining unauthorised access to corporate databases. Comprehending the distinctions between cybersecurity and information security is crucial for effectively safeguarding data from potential threats. The goal of cybersecurity is to defend networks against possible intrusions by utilising a range of instruments, including firewalls, antivirus software, and encryption techniques. By employing safe storage techniques like encryption and access control policies that restrict who can access particular kinds of information, information security focuses on safeguarding the data itself.
Risks to data security can take many different forms, including malicious software, online theft of private data, and even outsiders gaining unauthorised access to corporate databases. Comprehending the distinctions between cybersecurity and information security is crucial for effectively safeguarding data from potential threats. The goal of cybersecurity is to defend networks against possible intrusions by utilising a range of instruments, including firewalls, antivirus software, and encryption techniques. By employing safe storage techniques like encryption and access control policies that restrict who can access particular kinds of information, information security focuses on safeguarding the data itself.
Types of Digital Security Risks
An instance of a cyber threat to businesses is a malevolent assault on their computer systems. Phishing attempts and malware infiltrations that may cause financial loss or compromise private information are examples of this. Teams must be extremely watchful when keeping an eye out for any strange behaviour on their networks to prevent these kinds of attacks.
Strong cybersecurity protocols, which can identify threats promptly and assist in preventing them before any damage is done, can significantly lower the likelihood that such accidents will occur. Human mistake or carelessness is another kind of digital risk. This could result from staff members failing to adhere to appropriate cybersecurity procedures or from errors that could cause a system breach.
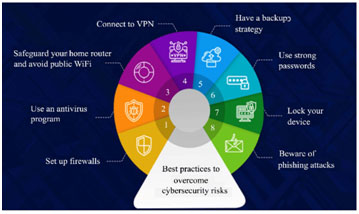 Organisations that want to reduce this kind of risk need to hire a Certified Cybersecurity Technician who can make sure all procedures are being followed correctly and invest in staff training programmes like Ethical Hacking Courses. Companies are greatly threatened by data security threats because they include hackers trying to access private data that is kept on network servers or cloud platforms.
Organisations that want to reduce this kind of risk need to hire a Certified Cybersecurity Technician who can make sure all procedures are being followed correctly and invest in staff training programmes like Ethical Hacking Courses. Companies are greatly threatened by data security threats because they include hackers trying to access private data that is kept on network servers or cloud platforms.
Organisations need to have robust backup plans and encryption capabilities in place to guard against this kind of assault and ensure that no private information is accessed without authorization from authorised staff members. It is also possible to make sure that all security procedures are appropriately followed and updated regularly in response to emerging risks by having frequent audits carried out by trained professionals.
The Benefits of Investing in Cybersecurity Training
 The hazards that hackers and other cybercriminals pose to people's data are becoming more well-known. Organisations are increasingly spending a lot of money on comprehensive cybersecurity training for their employees as a result. The risks posed by malevolent attackers can be lessened by making investments in a cyber security institute, an ethical hacking school, or even a trained cybersecurity technician.
The hazards that hackers and other cybercriminals pose to people's data are becoming more well-known. Organisations are increasingly spending a lot of money on comprehensive cybersecurity training for their employees as a result. The risks posed by malevolent attackers can be lessened by making investments in a cyber security institute, an ethical hacking school, or even a trained cybersecurity technician.
Investing in cybersecurity training equips staff members with the knowledge they need to safeguard not only their data but also the data of other individuals or companies, which is one of the biggest advantages. Employees who possess the necessary information are more equipped to comprehend and identify any threats to data security, including ransomware, malware infections, phishing schemes, and other illicit actions. These hazards can be recognised and averted before any harm is done with the appropriate training.
Another advantage of investing in cybersecurity training is that it helps organizations comply with compliance standards such as GDPR or HIPAA. Depending on the type of work an organisation does, it could be necessary to comply with specific regulations. Staff may be certain that they are adhering to compliance requirements and preventing any losses connected to customer data or other personal information by receiving thorough training regarding security policies and standards.
Staying abreast of the newest risks and trends in cybercrime enables organisations to maintain a competitive advantage in terms of online security. This not only gives their clients greater protection but also enables them to offer an all-around superior service. Keeping up with the latest developments in the digital world is crucial to preventing cyberattacks and other types of exploitation.
What Is Involved in an Ethical Hacking Course?
An in-depth understanding of cyber threats such as malware exploitation, network sniffing, social engineering threats, wireless network security problems, online application vulnerabilities, etc. is provided by an ethical hacking course. Topics include penetration testing techniques and test-related tools will also be covered in the course. Students also study how to recognise harmful code and analyse the activity of malware. Students who complete the course are awarded a certificate attesting to their expertise in ethical hacking procedures.
What to learn here:
 What is Ethical Hacking
What is Ethical Hacking- What are the different types of hackers
- Five phases of hacking
- Scope of Ethical Hacking
- Passive Information Gathering
- Active Information Gathering
- Scanning
- Introduction to Metasploit Framework
- Privilege Escalation
- Reverse TCP Connection
- Sniffing using Wireshark
- Cryptography
- Wireless Attacks
- SQL Injection Attacks
- IOT Hacking
- DOS Attacks and DDOS Attacks
- Cloud-based Attacks
Benefits Of Becoming a Certified Cybersecurity Technician
 The goal of a Certified Cybersecurity Technician (CCT) programme is to teach people the fundamentals of IT security, such as risk assessment standards for reducing cyber hazards. Through the programme, participants can learn how to set up firewalls and intrusion detection systems, which can help guard against malicious activities on a network or system.
The goal of a Certified Cybersecurity Technician (CCT) programme is to teach people the fundamentals of IT security, such as risk assessment standards for reducing cyber hazards. Through the programme, participants can learn how to set up firewalls and intrusion detection systems, which can help guard against malicious activities on a network or system.
What to learn here:
- Key issues plaguing the cybersecurity industry (information security and network security)
- Information security threats, vulnerabilities, and attacks
- Different types of malware
- Network security fundamentals
- Identification, authentication, and authorization concepts
- Network security controls
- Administrative controls (frameworks, laws, acts, governance and compliance program, and security policies)
- Physical controls (physical security controls, workplace security, and environmental controls)
- Technical controls (network security protocols, network segmentation, firewall, IDS/IPS, honeypot, proxy server, VPN, UBA, NAC, UTM, SIEM, SOAR, load balancer, and anti-malware tools)
- Network security assessment techniques and tools (threat hunting, threat intelligence, vulnerability assessment, ethical hacking, penetration testing, and configuration and asset management)
- Application security design and testing techniques
- Fundamentals of virtualization, cloud computing, and cloud security
- Wireless network fundamentals, wireless encryption, and security measures
- Fundamentals of mobile, IoT, and OT devices and their security measures
- Cryptography and public key infrastructure concepts
- Data security controls, data backup and retention methods, and data loss prevention techniques
- Network troubleshooting, traffic monitoring, log monitoring, and analysis for suspicious traffic
- Incident handling and response process
- Computer forensics fundaments, digital evidence, and forensic investigation phases
Conclusion
Any organisation must prioritise securing its cyber infrastructure, and part of that effort entails knowing the distinctions between information security and cybersecurity. Professionals are trained in ethical hacking courses and certified cybersecurity technician certification examinations by a team of industry specialists at the Cyber Security Institute. We are aware of the threats to data security and how to address them.
The extensive curriculum offered by the institute assists professionals in staying current with the most recent security threats and the methods for identifying and resolving them. With the aid of our knowledge base, you can create a thorough strategy for your company's defence against phishing scams, malware, data breaches, and other nefarious activity. In the end, in the current digital era, you must take the required actions to protect the cybersecurity of your company. With the right resources from the Cyber Security Institute, you can develop a plan that effectively addresses possible risks and raises staff awareness of safe procedures.
Hacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details
















