
Susmita: Oh, damn! Ankush didn't send the information that I asked him to send!
Zain: Look Susmita here is the most wanted document!
Susmita: What? Where? it's a cartoon image Zain! Are you kidding me?
Zain: No ma'am! He sent the most credential file keeping them inside such an ordinary file!
Susmita: But....... Why did he do this, and how????
Hey buddy, read the rest later! Are you extremely curious like Susmita too to know about hiding information? But what's the fact? To grasp this matter, you need to analyze the term Steganography. It is derived from Greek words. Stegano means concealed and graphein means writing. Let's understand this simple scenario.
Steganography is nothing but the practice of concealing messages, files, images, or any kind of data within another message, files, images, or another data without using an encryption method.
"It is the art and science of embedding secret messages in cover message in such a way that no one, apart from the sender and intended recipient, suspects the existence of the message."
Let's throw a look at its historical view. The first recorded uses of Steganography can be traced back to 440 BC when Herodotus mentions two examples in his history. Histiaeus sent a message to his vassal, Aristagoras, by shaving the head of his most trusted servant, "marking" the message onto his scalp. Then sent him on his way once his hair had regrown, with the instruction, "When thou art come to Miletus, bid Aristagoras shave thy head and look thereon."
The ancient practices of these techniques are – wax tablets, invisible ink, null cipher, microdots, semagrams, etc. Historical happenings surely attract you. So, let's find out what happened.
- Wax Tablet – The king of Sparta sent a secret message on a tablet covered with wax.
- Invisible Ink – It was the most common and fascinating technique. The actual message could be visible if a document is heated gently.
- Null Cipher – It referred to a method of encrypting where plain text is mixed with an actual message.
- Microdots – This was used for concealing data. It is a simple text or an image that is reduced in size to hide its content.
Now, steganography is evolved as a multimedia object and has been majorly used digitally.
There are 4 popular types of steganography.
- Text Steganography
- Image Steganography
- Video Steganography
- Audio Steganography
Let me give you some basic ideas about these four techniques.
1. Text Steganography
This kind of steganography is a mechanism for hiding private text messages inside another text as a covering message. There are three main categories used in text steganography.
- Random and Statistical Generation: This kind of text steganography automatically produces the cover text image without the need for an existing cover message.
- Linguistic Methods: This method is used for hiding a message in another message depending on the linguistic structure of the cover message. Here are two main types.
- Linguistic Structure: In this technique, the cover message must have punctuation marks. These marks are the identification symbol for the hidden message.
Drawback – Data size depends on the number of punctuation marks on the cover message. - Semantic Method: In this steganography technique, the synonyms of each word are used to hide the private message and also to generate the output cover message.
Drawback – Failed in protecting the sent message when the outsider tries to find the actual message by swapping each word to the original one using semantic algorithms.
- Linguistic Structure: In this technique, the cover message must have punctuation marks. These marks are the identification symbol for the hidden message.
- Format Based: In this text steganography technique, the covering message will not be altered in the case of its words and sentences. Just modification is needed between the words, lines, or paragraphs using special characters or white-space steganography.
Some of you may not be familiar with semantic algorithms and white-space steganography.
Semantic algorithm: It is such an analysis which helps to find out the actual meaning of the text. It is considered a crucial part of NLP. This algorithm allows machines to grasp and expound sentences or entire documents by figuring out their grammatical structure and recognizing relationships between individual words in a specific context. Semantic analysis is based on hyponyms, meronomy, polysemy, synonyms, antonyms, and homonyms.
White-space steganography: It is used to hide messages in ASCII text by conjoining whitespace to the end of lines, spaces or tabs.
Now let's come to other parts of steganography.
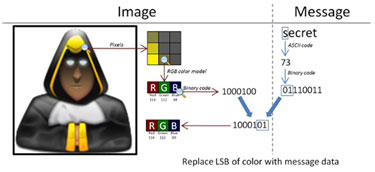
2. Image Steganography
In this type of steganography, hidden data is implanted into an image by changing the values of digital representation. There are a lot of ways used here. One common approach is – LSB steganography, masking and filtering, and many others.
Want to know about LSB (Least Significant Bit) steganography? Cool Boss! Before that, let me give you a basic idea about the colour model. What is colour model, sir?
It is a method for creating a whole range of colours from a set of primary colours.
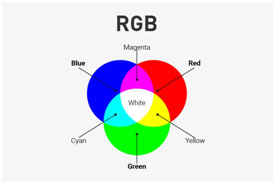 In computer graphics, one of the most additive colour models is RGB (Red, Green, Blue) colour model. It is used in display monitors.
In computer graphics, one of the most additive colour models is RGB (Red, Green, Blue) colour model. It is used in display monitors.
We are working with RGB here. Pixel is nothing but the smallest addressable element in a raster image. Each pixel has its colour and individual digital representation.
Importance of RGB Model:
- Used for hardware applications like PC monitors, scanners, TV
- Used for web graphics but can't be used for print production
- It directly reflects the physical properties of the "True-colour" display
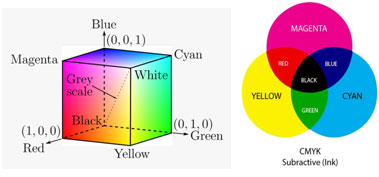 Another popular model is – CMY (Cyan, Magenta, Yellow) colour model which is used in the printer. CMYK (Cyan, Magenta, Yellow, and Key (Black)) model works partially or entirely masking colours on a lighter e.g., white background.
Another popular model is – CMY (Cyan, Magenta, Yellow) colour model which is used in the printer. CMYK (Cyan, Magenta, Yellow, and Key (Black)) model works partially or entirely masking colours on a lighter e.g., white background.
Importance of CMY/CMYK Model:
- CMY/CMYK is a subtractive colour model which is used for offset printing colours perceived in this model are the result of reflected light.
- This model is used in electrostatic and inkjet plotters which deposit the pigmentation on paper.
- The specified colour is subtracted from the white light rather than adding blackness.
- It follows the cartesian coordinate system and its subset is a unit cube.
Hope you will not have any problems this time in understanding LSB Steganography.
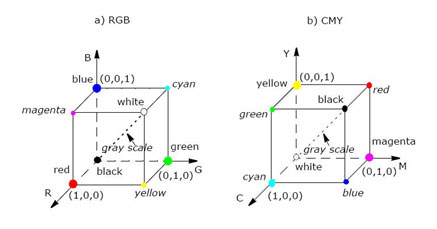
LSB stands for Least Significant Bit. Computer information is stored in bits that make up bytes and only significant means that we are going to choose to change or modify the bit at least affect the image. We can take an example!
Suppose, 10101001. So, here are multiple bits where,
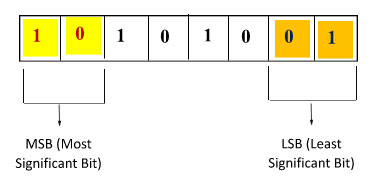
So, what are we doing with these two last bits? That's the main part of Least Bit Steganography.
Say, if you have an image and this has a lot of pixels where each pixel has colour. This image may follow any colour model. Let's take RGB Colour Model. Using this model, we can get any colour.
- Red: RGB (255,0,0) – RGB (11111111, 00000000, 00000000)
- Green: RGB (0,255,0) – RGB (00000000, 11111111, 00000000)
- Blue: RGB (0,0,255) – RGB (00000000, 00000000, 11111111)
Using this, we can get multiple complexes of colours by adjusting the values. This is the fundamental idea behind understanding LSB Steganography. Let's take an example!
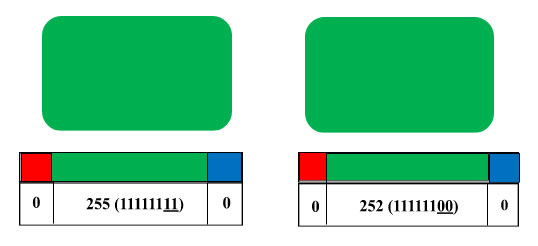
 You may find similarities between these two images from the angle of their colour. But if you look at their colour values, you will notice a slight change in the green parameter.
You may find similarities between these two images from the angle of their colour. But if you look at their colour values, you will notice a slight change in the green parameter.
It is 252 instead of 255, so this is not a pure green colour. Here, in the second image's colour value, 00 is the Least Significant Bit.
So, what can we do with these two bits? We can use this for storing the information. The image may be the same but hidden messages are in these two portions. We can also reserve these two bits in the red parameter as well as in the blue parameter. So, we can store data in this place and that's why the Steganographic technique involves this idea called LSB Steganography.
We can modify the Least Significant Bits so that viewers won't find many colour differences but still data is hidden! There is also a Palette-Based Technique that relies on images. Crackers embed this technique as GIF files.
Drawback
- Bit quality will be changed.
- Many applications are there to analyze the existence of secret messages in an image by comparing the pixels of the original image with the received image.
- Limitations of binary string length, size, and number of pixels in the image.
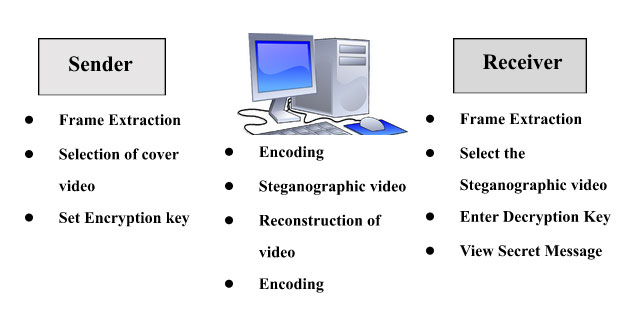
3. Video Steganography
Here, the secret video is hidden inside the cover video to produce the steganographic video.
4. Audio Steganography
Secret message in audio! Maybe you have a lot of thoughts running through your head at once.
 How to hide any secret data in any audio file?
How to hide any secret data in any audio file?
How to view secret data hidden in an audio file?
How to decrypt the secret data? ….. and many more. Not you!
Yes, you can apply this technique too! It's not that you are changing the file extension. There must be audio and secret data inside it.
As you learn about Steganography, know its advantages and disadvantages thoroughly!
Advantages of Steganography in Information Security:
- Hard to detect the secret information
- Maintains invisibility
- Protect copyright
- Able to create Peer-to-Peer private communications
Disadvantages of Steganography in Information Security:
- Loss of integrity
- Possibility of data loss
- Degradation of an image
- Sometimes original messages may be detected by hackers before it is received by the receiver
Conclusion
Steganography is completely a part of Ethical Hacking. A solid and easy technique for hiding secret any kind of data or message overlaying it with a funky or noisy message, image, audio, or video. It's nothing but a hint to let you know. Hushhh! Hackers are watching and may even be listening
Hacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details
















