
Apple, the American IT multinational, offers bug bounty to award researchers for reporting crucial technical issues and the modus operandi to exploit them besides resolving the vulnerability to optimize effective cyber security.
There is good news of every ethical hacker!
And a bad news for his unethical counterpart.
Apple, the global brand of consumer electronics, computer software, and online services, as a part of its Corporate Social Responsibility, offers a compensatory package to researchers worldwide in order to ensure ultimate cyber security and safe internet experience of its clients and users in general.
It offers cyber security researchers and ethical hacking enthusiasts around the world a lucrative financial reward for reporting bugs, security vulnerabilities and other internet safety issues. The issues are then rightly solved followed by acknowledgement of the qualifying researcher and charity donations matching the magnitude of the bounty.
What are the eligibility criteria for this bug bounty program of apple?
A generic criterion for eligibility in the Apple Security Bounty is that the vulnerability must appear in the latest publicly available versions of iOS, iPadOS, macOS, tvOS, or watchOS with a standard configuration and, where applicable, on the latest publicly available hardware.
The strict selection rules ensure customer protection till an update is developed. It is all directed at Apple's ability of prompt verification of the report, designing necessary updates and acknowledging the reporter of the original research appropriately.
The researcher has also to abide by the following:- He has to be the first one to report the issue to Apple Product Security.
- He has to provide a clear report which must include a working exploit.
- He cannot let the issue be known publicly before Apple releases the security advisory for the report. Normally, the advisory is released along with the related update to resolve the issue.
In case of issues unknown to Apple and exclusive to designated developer betas and public betas, including regressions, a 50% of bonus is payable.
The issues that are eligible are as follows:- Security issues propagated in certain designated developer beta or public beta releases. Not all developer or public betas are eligible for the excess bonus.
- Regressions of previously resolved issues including those with published advisories that have been reintroduced in a developer beta or public beta release.
Rules regarding Report and Payout
The idea behind the Apple Security Bounty is ultimate consumer safety by understanding both vulnerabilities and their exploitation techniques. Reports that consist of a basic proof of the bug and not any working exploit will get only 50% of the bounty offer. Reports that don't have the much needed data for Apple to effectively work upon the issue will be rewarded lesser the amount appropriately, if accepted at all.
A complete report is characterized by- An elaborate description of the issues being reported.
- Any criteria or procedure to get the system to an impacted state.
- An appropriately dependable exploit for the issue being reported.
- Adequate data for Apple to effectively reproduce the issue.
Maximizing the bonus
In order to optimize the bug bounty the researcher must report about issues that:- Affect multiple platforms.
- Affect the most modern publicly available hardware and software.
- Are exclusive to newly added features or code in designated developer betas or public betas, including regressions.
- Impact sensitive components.
- Are original.
Additional Requirements
In addition to a complete and comprehensible report issues that need the execution of multiple exploits as well as one-click and zero-click issues require a full chain for optimum bonus. The chain and report must include:- Both compiled and source versions.
- All that is required to execute the chain.
- A sample non-destructive payload, if needed.
Sending Your Report
Send your report by email to [email protected].
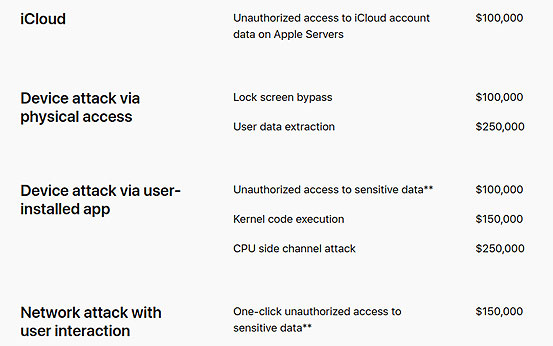
A cross section of issues and the magnitude of bounties they attract are as follows:
We are living in a world ruled by the internet. A trend that started at the turn of the new millennium has become a style of life today. But as all silver clouds have a dark lining, the fast and easy cyber world too is dominated by hackers who are out in the wild to wreck havoc. ISOEH has been the original name in combating cyber threats with its ethical hacking curriculum.
If you wish to participate in the apple bug bounty program and earn 1 million dollars, you need to know iOS penetration testing.
Do you think ethical hacking and cyber security is coming up in a big way as a lucrative career for the young and enthusiasts? Tell us.
Hacking Tools
Explore All Hacking Tools »
UFTP is an encrypted multicast file transfer program for secure, reliable & efficient transfer of files. It also helps in data distribution over a satellite link.
Read DetailsBreaking News
Breaking News Of Each Month »
The recent pandemic was unexpected and unknown to most part of the world. It has changed our life and we are slowly adapting to our new lifestyle. The risks associated with the new lifestyle, both personal & corporate, are unknown to most of us.
Read Details















