The Certified Penetration Testing Professional or CPENT for short, is rewriting the standards of penetration testing skill development. The key philosophy behind the CPENT is simple – a penetration tester is as good as their skills. That's why we urge you to go beyond Parrot and beyond tools. Another thing that makes this program unique is that you get a chance to attain two certifications with just one exam: the CPENT and the LPT (Master). Take the CPENT exam and score better than 70% and you earn the CPENT. If you score over 90%, you earn the highly-coveted LPT (Master) certification!
Why learn CPENT?
Overcoming the
Real World Situations
Inclusive of all the
Latest And Advanced Topics
What Makes The Certified Penetration Testing Professional (CPENT) Unique?

Duration
4 hours x 10 days
Weekend, evening, weekdays - Classes Available
Eligibility
Course Fees
Class Room Training
Rs.45,500/-
+ 18% GST
Online Training
Rs.55,500/-
Rs.45,500/-
+ 18% GST
What You Will Get?
10 Days
of in depth training by the best cyber security experts
Study Materials
and examination voucher
CPENT
Certificate of Completion after examination and alumni status
Important Notice for International Students: The EC-Council global course fee and Exam Voucher fee will depend on the candidate's location and foreign currency exchange rate.
Course Benefits:
- Cost effectiveness
- Industry accepted
- Global recognition
A Hands-On Exam Like No Other:
24 Hours will define your Pen Testing career

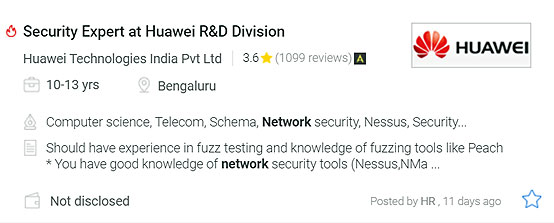
CPENT is a fully online, remotely proctored practical exam that challenges candidates through a gruelling 24-hour performance-based, hands-on exam. The exam is broken into 2 practical exams of 12-hours each that will test your perseverance and focus by forcing you to outdo yourself with each new challenge. Candidates have the option to choose either 2 12-hour exams or one 24-hour exam.
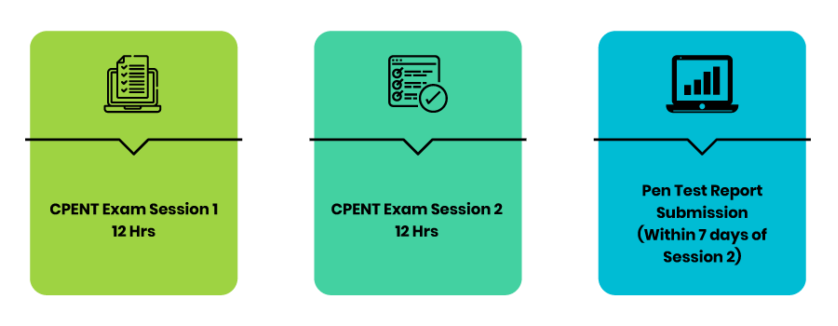
Candidates who score more than 70% will earn the CPENT certification. Candidates who score more than 90% attain the prestigious LPT (Master) credential!
Exam features:
- Choose your challenge! Either two 12-Hour sessions or a single 24-Hour exam!
- EC-Council specialists proctor the entire exam – cheating is not an option.
- Score at least 70% and become a CPENT.
- Score at least 90% and earn the highly regarded LPT (Master) designation!
Your Course Path
Course Details
- 100% mapped with the NICE framework
- Comes blended with both manual and automated penetration testing approaches
- Maps to the job role of a penetration tester and security analyst, based on major job portals
- Gives a real-world experience through an Advanced Penetration Testing Range
- 100% methodology-based penetration testing program
- Is designed based on the most common penetration testing services offered by the best service providers in the market
- Provides strong reporting writing guidance
- Offers templates that can be used to conduct pen tests in the wild
Hacking Tutorials
Read All Tutorials »
Building a career in Digital Forensic - How promising is the future? A thorough career guide
Read Details »Hacking Videos
Explore All Videos »How to Hiding Your Secret File using Steganography?
View On Youtube »Enroll Now
Fields marked with * are mandatory.
Ratings & Reviews
How CPENT Transformed Careers: Success Stories of Cyber Security Professionals
Job Prospects & Job Sources
The Profiles that count for CPENT Certified Individuals include the following:
| Penetration Testers | Ethical Hackers | Information security Consultant |
| Security Testers | Security Analysts | Security Engineers |
| Network Server Administrators | Firewall Administrators | System Administrators |
| Risk Assessment Professionals |
The average salary of CPENT IT employee in India is Rs 18 lakhs per annually.
FAQs
The CPENT range consists of entire network segments that replicate an enterprise network — this is not a computer game simulation; this is an accurate representation of an enterprise network that will present the latest challenges to the pen tester. The benefit of hands on learning in a live cyber range is that candidates will encounter multiple layers of network segmentation, and the CPENT course will teach candidates how to navigate these layers, so that once access is gained in one segment, a candidate will know the latest pivoting techniques required to reach the next. However, that won’t be enough on its own as the targets and segments are progressive in nature, so once you get into one machine and or segment, the next one will challenge you even more!
You have the potential to earn two certifications with one exam. If you score above a 90% on the CPENT live range exam, not only will you earn the CPENT certification, but you will also earn the Licensed Penetration Tester (LPT) Master Credential!
To be a LPT (Master) means that you can find chinks in the armor of defense-in-depth network security models with the help of network pivoting, making exploit codes work in your favor, or by writing Bash, Python, Perl, and Ruby scripts. The live range CPENT exam demands that you think on your feet, be creative in your approach, and not rely on the conventional techniques.
Outsmarting and out maneuvering the adversary is what sets you apart from the crowd. The CPENT’s hands-on exam offers a challenge like no other by simulating a complex network in real time. This experience will test your perseverance and focus by forcing you to outdo yourself with each new challenge.
LPT (Master) certified professional can:- Demonstrate a repeatable and measurable approach to penetration testing
- Perform advanced techniques and attacks to identify SQL injection, Cross site scripting (XSS), LFI, RFI vulnerabilities in web applications
- Submit a professional and industry accepted report that achieves management and technical buy-in
- Get access to proprietary EC-Council penetration testing methodologies
- Write exploit codes to gain access to a vulnerable system or application
- Exploit vulnerabilities in Operating systems such as Windows, Linux
- Perform privilege escalation to gain root access to a system
- Demonstrate ‘Out-of-the-box’ and ‘lateral’ thinking
- Ensure the integrity and value of the penetration testing certification, in a fully online, remotely proctored certification exam
The CPENT program is the next step after the Certified Ethical Hacker (CEH) certification on the journey to the Licensed Penetration Tester (LPT) Master. There is a lot of chatter out in “the ether” that refers to CEH as a Pen Test program. That information is not correct. The CEH course was designed to teach the tools and methods deployed by cyber criminals.
The CPENT and its now-retired predecessor courses, the EC-Council Certified Security Analyst (ECSA) and the Advanced Penetration Tester (APT), are pen test courses that were designed to take the concepts taught in CEH and apply them to time-proven pen test methodologies.
- 100% mapped with the NICE framework.
- 100% methodology-based penetration testing program.
- Blends both manual and automated penetration testing approaches.
- Designed with the most common penetration testing practices offered by the best service providers.
- Maps to all major Job Portals. Role Title: Penetration Tester and Security Analyst.
- Provides strong reporting writing guidance.
- Gives a real-world experience through an Advanced Penetration Testing Range.
- Provides candidates with standard Pen test for use in the field.
- Advanced Windows Attacks:
This zone contains a complete forest that you first have to gain access to and then use PowerShell and any other means to execute Silver and Gold Ticket and Kerberoasting. The machines will be configured with defenses in place meaning you to have to use PowerShell bypass techniques and other advanced methods to score points within the zone. - Attacking IOT Systems:
CPENT is the first certification that requires you to locate IOT devices and then gain access to the network. Once on the network, you must identify the firmware of the IOT device, extract it, and then reverse engineer it. - Writing Exploits: Advanced Binary Exploitation:
Finding flawed code is a skill competent pen testers need. In this zone you will be required to find the flawed binaries then reverse engineer them to write exploits to take control of the program execution. The task is complicated by the requirement of penetrating from the perimeter to gain access then discover the binaries. Once that is done you have to reverse engineer the code. Unlike other certifications, CPENT includes 32 and 64 bit code challenges and some of the code will be compiled with basic protections of non-executable stacks. You must be able to write a driver program to exploit these binaries, then discover a method to escalate privileges. This will require advanced skills in binary exploitation to include the latest debugging concepts and egg hunting techniques. You are required to craft input code to first take control of program execution and second, map an area in memory to get your shell code to work and bypass system protections. - Bypassing a Filtered Network:
The CPENT certification provides web zone challenges that exist within a segmentation architecture, so you have to identify the filtering of the architecture then leverage this knowledge to gain access to web applications. The next challenge is to compromise and then extract the required data from the web apps to achieve points. - Pentesting Operational Technology (OT):
The CPENT range contains a zone that is dedicated to ICS SCADA networks that the candidate will have to penetrate from the IT network side and gain access to the OT network. Once there, you will have to identify the Programmable Logic Controller (PLC) and then modify the data to impact the OT network. You must be able to intercept the Mod Bus Communication protocol and communication between the PLC and other nodes. - Access Hidden Networks with Pivoting:
Based on our beta testing, pen testers struggle to identify the rules that are in place when they encounter a layered network. Therefore, in this zone you will have to identify the filtering rules then penetrate the direct network. From there, candidates have to attempt pivots into hidden networks using single pivoting methods, but through a filter. Most certifications do not have a true pivot across disparate networks and few (if any) have the requirement into and out of a filtering device. - Double Pivoting:
Once you have braved and mastered the challenges of the pivot, the next challenge is the double pivot. This is not something that you can use a tool for; in most cases the pivot has to be set up manually. CPENT is the first certification in the world that requires you to access hidden networks using double pivoting. - Privilege Escalation:
In this challenge, the latest methods of privilege escalation reverse engineering code to take control of execution then break out of the limited shell are required to gain root/admin. - Evading Defense Mechanisms:
The range requires your exploits be tested by different defenses you are likely to see in the wild. Candidates are required to get their exploits past the defenses by weaponizing them. - Attack Automation with Scripts:
Prepare for advanced penetration testing techniques and scripting with seven self-study appendices: Penetration testing with Ruby, Python, PowerShell, Perl, BASH, Fuzzing, and Metasploit. - Weaponize Your Exploits:
Customize your own tools and build your armory with your coding expertise to hack the challenges presented to you as you would in real life. - Write Professional Reports:
Experience how a pen tester can mitigate risks and validate the report presented to the client to really make an impact. Great pen testing doesn’t mean much to clients without a clearly written report!
- Ethical Hackers
- Penetration Testers
- Network server administrators
- Firewall Administrators
- Security Testers
- System Administrators and Risk Assessment professionals
- Cyber Security Forensic Analyst
- Cyber Threat Analyst Tier 2
- Cyber Threat Intelligence Analyst
- Information Security Analyst
- Cyber Security Engineer
- Application Security Analyst II
- Cyber Security Assurance Engineer
- Senior Information Assurance/ Security Specialist
- Security Systems Analyst
- Security Operations Center (SOC) Analyst
- Penetration Tester
- Technical Operations Network Engineer
- IT Security Administrator
- Security Engineer
- Information Security Engineer
- Network Security Information Analyst
- Mid Level Penetration Tester
- IT Security Analyst III
- Junior Security Operations Center (SOC) Analyst
Member of: